| Home | The Book | Training | Events | Tools | Stats |
January 15, 2013
An ADP Malware Lure
Payroll is one of the most important parts of any multi-employee business. It can also be a regulatory nightmare. It's fairly common, then, for businesses large and small to contract out the job to third parties. One well-known firm that handles payroll and other human resources tasks is ADP. Writing or authorizing payroll checks means direct access to at least one corporate bank account by at least one person in the company. If a company relies on ADP to manage payroll and issue checks, then the person responsible for communicating with ADP will certainly pay attention to an email that purports to originate from ADP.
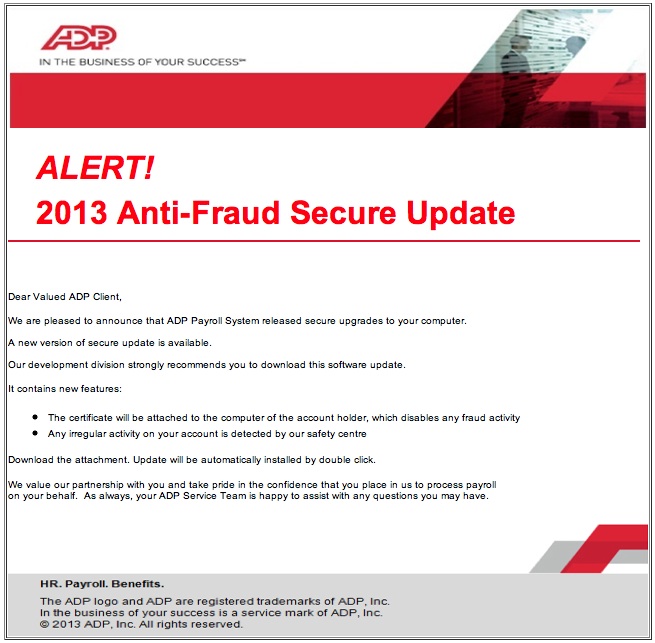
And thus we come to a bogus email campaign spreading today. The message is all up in the recipient's face about an update intended to fight fraud. Here is the message:
Although there is a little bit of confusion about downloading and an attachment, I can easily envision an unwary recipient ADP customer opening the 2013 Anti-Fraud Secure Update.zip attachment. Since the computer being used to manage the ADP relationship is likely used for other financial transactions in the company, the malware that gets loaded from the attachment (and subsequent ownership by the trojan thus installed) means that login credentials will soon be lifted and accounts cleaned out.
Even if you're not an ADP customer, curiosity will kill login credentials for all types of sites you visit. The slurping sound you hear is your high-value accounts being drained.
Sadly, this particular file has, at this hour, a very low AV detection rate (7 of 46) at VirusTotal. My own computer's Sophos AV software does not yet recognize it as being hazardous.
As usual, the best defense against this kind of attack is 100% suspicion of any email message claiming to come from a web site where you have an account — especially financial sites and shopping sites where your credit card is on file. Always use pre-existing bookmarks to visit a site if you receive some kind of warning or alert from that site via email. If there is a genuine problem with your account (highly unlikely), you'll learn about it at login time.
January 11, 2013
English as a Tenth Language
Wow! Today's alleged Intuit Payroll Services alerts are doozies. So far, not one of the messages has had the From: field tied to Intuit. There is Friendster Games and tons of LinkedIn-related addresses. It just gets worse from there:
Subject: Payroll Account Holded by Intuit
[Real Intuit logo sourced from intuit.com]
Direct Deposit Service Informer
Communicatory Only
We cancelled your payroll on Fri, 11 Jan 2013 11:43:57 +0300.
- Finances would be gone away from below account # ending in 0083 on Fri, 11 Jan 2013 11:43:57 +0300
- amount to be seceded: 5133 USD
- Paychecks would be procrastinated to your personnel accounts on: Fri, 11 Jan 2013 11:43:57 +0300
- Log In to Review Operation
Funds are typically left before working banking hours so please make sure you have enough Finances accessible by 12 a.m. on the date Cash are to be seceded.
Intuit must reject your payroll by 4 p.m. Central time, two banking days before your paycheck date or your state would not be paid on time.
QuickBooks does not process payrolls on weekends or federal banking holidays. A list of federal banking holidays can be viewed at the Federal Reserve website.
Thank you for your business.
Regards,
Intuit Payroll Services
As usual, links go to hijacked web site pages that redirect to a different site where malware loading begins. I've seen plenty of machine-translated attempts in malware spam before, but this guy manages to make up words. Holded?
Wow!
Posted on January 11, 2013 at 09:40 AMJanuary 08, 2013
A Portuguese Deposit
Want to see what a malware lure looks like in Portuguese? Here ya go:
From: Kelin-gol
Subject: depositoOi, sexta-feira fiz um depósito em sua conta, só que foi errado, não era pra você, estou enviando o comprovante para você dá uma olhada, queria que você me devolvesse o valor, pois foi uma falha da minha assistente, peço mil desculpas pelo transtorno.
Me ajuda por favor e desde já agradeço a sua colaboração!
Deposito_sexta.zip
Abraços
And here is the English machine transation:
Hi, Friday made a deposit into your account, except that it was wrong, it wasn't for you, I am sending the voucher for you take a look, I wanted to let you return the value, as it was a failure of my assistant, ask a thousand apologies for the inconvenience.Please Help Me and I thank you for your collaboration!
Deposito_sexta.zip
Hugs
The link is to a Dropbox account that automatically downloads a .zip file containing well-recognized malware. A helpful little email that is out to capture your PC.
Hugs.
Posted on January 08, 2013 at 12:21 PM
I've seen a few instances of a malware delivery email message that might trip up a number of recipients.
Here is the first version:
From: Alkharji Trade Co UAE Subject: Product EnquiryDear Sir/Madam,
We are interested in purchasing your products and we sincerely hope to
establish a long-term business relation with your esteemed company.
Please kindly view our samples HERE and HERE then send me your latest catalog. Also, inform me about the Minimum
and maximum Order Quantity, Current Delivery time or FOB, and also current
payment terms warranty.
Your early reply is highly appreciated.
Kind Regards,
Ahmed
The links in the message lead to SendSpace (and one URL was malformed to omit the ".com", so that will certainly hurt their efficiency...boo hoo), where the files are named sample1.zip and sample2.zip. Sadly, both files came up squeaky clean on VirusTotal. But both files expand to .exe files. One had fair coverage in VirusTotal (although many big-named AV products didn't recognize the files as malware over 12 hours later), while the other was recognized by only one AV vendor.
Another variant this morning has the same basic theme, but the zipped files are attached to the email message.
If you have been in business for as long as I have, you are familiar with these kinds of blind product information requests arriving from time to time. But this one won't lead to any business. Instead, its files will give you the business...if you know what I mean.
Posted on January 08, 2013 at 11:04 AM