| Home | The Book | Training | Events | Tools | Stats |
December 30, 2007
"This is Not Spam" and Other Lies
Amid the flurry of New Year greetings desperately trying to get me to download a Trojan "postcard" came an unsolicited message trying to sell me electronic goodies. It begins:
This is not spam. You can subscribe to this list or remove from this list at your will.
After a slew of product listings, comes more disclaimer stuff (copied ver[sic]em):
You received this email because you have subsribed to our mailing list at one point. Our philosophy is to inform the customers not spam them. We will NOT send you more than two emails within any 7 day period (think about some of the spam emails that you might receive everyday). If you don't want to receive our emails in the future, it is also very easy to do. goto our unsubscribe website, fill in your email address and the email identifier, then submit the request. We use a unique identifier to prevent people from unsubsribing others simply by knowing their emails. If you don't have an email identifier, you can get one from the same place.Please note that it might take a few days to unsubscribe, but in general you will not receive any more messages.By the way, please dont reply to this message. The email account is not monitored and any email will be deleted without reading.
The minute a marketer tells you that the message is not spam, you know instantly that it's spam. In your eyes, anyway. It's like that old joke, "We're from the government, and we're here to help." Things can only get worse from that point onward.
The sender believes that by simply providing an opt-out mechanism, the message complies with the U.S. CAN-SPAM law. But, as we all know, just because it's "legal" doesn't make it not spam in the eyes of the recipient. Moreover, he fails to identify himself in the message, using a yahoo.com address in the From: field. There is no business name or address at all. That's definitely illegal.
He also blew it Big Time by sending the message to an address of mine that could have been obtained only by harvesting from a third-party web site. The address is used for absolutely no other purpose. Whether he did the (also illegal) harvesting or bought the list from someone else who plucked the address, I can guarantee you that I never submitted that address to sign up for marketing mailings (either subscribe, or, as he writes, "subsribe") or to conduct any other business with a web retailer.
So, it appears we have here your basic run-of-the-mill spammer. Pardon me while I yawn.
But then I checked out the links in the message. The subscribe/unsubscribe links are to a domain whose name promises me bargains on the web. But the product links are to amazon.com searches (tagged with an identifier) and to an Amazon service called aStore. From my understanding, aStore makes it easy to set up a finely-tuned web shop that pulls from Amazon's inventory, uses Amazon's shopping cart, and more.
I couldn't imagine that Amazon would condone the use of spam—especially illegal spam—to attract customers to click on links that generate business for one of its Associates. Navigating to the Associates Operating Agreement, I found Section 11, which states, in part:
...you agree that as a condition of your participation in the Program you will comply with all applicable laws (federal, state or otherwise) that govern marketing email, including without limitation, the CAN-SPAM Act of 2003 and all other anti-spam laws.
That, along with the Associates program identifier for this rube buried within his links, was everything I needed to know, so I submitted my report to the Associates support department. Having just gone through a less-than-satisfying experience with one giant company, I had my doubts. The only thing going for me is that the Associates program must be a smaller business unit within the giant Amazon corporation.
Much to my surprise and glee, I received a response in less than six hours (on a Saturday), which read, in part:
We were unaware of this Associate's intention to advertise in this manner and would certainly never have pre-approved it. We do not use nor tolerate the use of spamming as an advertising method. We will contact the offender immediately and put a stop to this.
Although I would have preferred putting a stop to the offender (my dream world has a one-strike-and-yer-out policy about spam and any financial benefit derived therefrom), putting the guy on notice is a decent first step. I included the full source code of the spam message, but blocked out the harvested email address. Thus, in case Amazon sends him a copy of my report, he won't be able to listwash my address. Any future attempts to spam to that same list will reach me, and trigger yet another report to Amazon and, with luck, bring the hammer down.
How's that for a web bargain, jerk?
Posted on December 30, 2007 at 02:41 PMDecember 24, 2007
Argh! The Frustration of Big Companies
Trying to report abuse to some organizations can drive the reporter to drink (or, in my case, chocolate).
I'll begin by saying that I understand it is necessary for organizations with gigantic user bases to have ways to handle the 90% of support questions that have been asked and answered in Frequently Asked Questions areas and other online support documents. I grant you that the bulk of support questions that come in are sent by those who are too lazy to search the archive or don't know how to phrase the question. Spending corporate support dollars on staff to answer the same questions over and over must take a low priority. I even saw an ISP's site today that explicitly tells visitors that there is no email contact address for the Support Department—you must be a customer and follow the Yellow Brick Road through its automated help facilities.
Whenever I take the time to report alleged abuse to a company, I perform some due diligence ahead of time. I try to be as accurate and succinct as possible in my report. In sympathy for the overloaded recipient of my report, I get to the point and supply all necessary documentation to help them get to the source of the issue quickly.
The problem with companies who receive huge amounts of support queries is that in so many cases, they don't even seem to read my subject line, much less the brief summary of my issue. In return for my researched report, I receive a form reply answering a question that had nothing to do with my report.
Here's the latest:
On December 21, 2007, I received a typical PayPal phishing message. In checking the content of the target page (without rendering it), I saw something very out of the ordinary for phishing. The page's content was created entirely using an encoded JavaScript technique very common to malware installer pages.
I captured the script and evaluated it without rendering the HTML results. Had the page rendered in a browser (as would happen with any visitor from the phishing message who had JavaScript enabled in the browser), it would have triggered a URL to googlesyndication.com. Whoa, Nellie!
Google, itself, was no help in leading me to find out what this could be, although I suspected it had something to do with advertising, probably through Google's AdSense service. I did some more digging elsewhere and learned (possibly) that links to googlesyndication.com cause the click-on-the-ad counter to fire before navigating the user to the advertiser's site. My suspicion, therefore, was that anyone who followed the phishing message's link, visited a page whose mere visit caused an ad click counter to fire, putting money into the crook's pocket (and stealing it from the advertiser and Google).
Click fraud is supposedly a pretty big deal in the high-volume Internet advertising business. I read about it all the time in mainstream business press. Advertisers fear it, and the ad-serving sites (like Google's AdSense) reassure advertisers that they're doing everything possible to counter the fraud. Thus, I thought Google's AdSense program might be interested in this potential fraud technique.
I found a Support area at Google's site, where I could choose the AdSense Program as the target of my support query. They actually provided an email address to which I could address my "question." The Subject: line of my message was far from ambiguous:
Possible abuse of googlesyndication.com
In the body of the message, I included the rendered version of the encoded JavaScript, which included identification numbers of the advertiser and commission earner in plain HTML. And, because I'm not an AdSense guru, I made my accusation in the following manner:
If rendering this page causes the issuer to earn a commission from a Google advertiser upon display of the ad, then he used fraudulent means to obtain that ad display and commission.
I then also included the source code of the phishing email message for good measure.
So, there it was. I had presented my case and provided enough evidence for Google to look into it.
Three days later (not too bad for a Big Company), I received a response, which began:
Hi,Thanks for your email. We'll be more than happy to provide you with
information on your AdSense earnings.
This was followed by a bunch of standard support questions and answers related to viewing AdSense earnings.
Hello? Earth calling Google!
I have some Qs for which I doubt I'll ever receive As:
- Did a human read my original message?
- If so, was that person awake/alive at the time?
- If this is a completely automated response, why did it take three days to respond?
- If I was wrong in my accusation, can you simply tell me that my fears are unfounded?
- Do you really give a Rémy's ass about click fraud?
As for what this episode means for everyday email users, the point is that clicking a link in any unsolicited email message can put money into the crook's pocket, even if you don't hand over any personal info (which this "phisher" didn't even want).
As for me on this Christmas Eve, I'm sending a big "Bah, humbug!" down to Mountain View, CA.
Posted on December 24, 2007 at 10:36 AMDecember 23, 2007
Phishers Are Too Cheap to Hire a Copy Editor
Whenever I see some tortured gobbledygook trying to pass as earnest English, my mind flips to a scene in the 1966 comedy film The Russians Are Coming! The Russians Are Coming! In the film, a Soviet submarine accidentally runs aground off a small New England village, and a crew tries to get help from locals without raising too much of a ruckus. In their efforts to keep bystanders from seeing activity that could spark an international incident, one crew member who knows a little English teaches his shipmates how to warn passersby to stay inside their homes. They master this sentence, which they all repeat with very heavy Russian accents:
Emergency! Everybody to get from street!
That's how I remember it, anyway.
Today's installment of fractured English arrives courtesy of a PayPal phisher:
Important Security Update
Dear PayPal member:Paypal has the last days updated all user account with better security to avoid unwanted access and to reduce the instance fraud to keep our users information secure, Some user accounts lost there information while new security update was complete, we are realy sorry about this problem.
Can you take 5-10 minutes of your time to make sure your account information is correct so we can continue our service for you.
Press the link below to update your personal paypal account.
http://www.paypal.com/ [hidden link to phony site]If you have experience any problems with your email or password press this link to report the problem to our support.
Report Login Problem To Support [hidden link to phony site]PayPal, Inc.
P.O. Box 45950
Omaha, NE 68145Sincerely,
PayPal
I was going to mark up this message to highlight all the grammatical and punctuation errors. But then I figured that I'm not being paid to be a copy editor for criminals. Screw 'em.
This phisher isn't a complete idiot. He did try to obfuscate the message by encoding its content (thereby trying to keep from being blocked by phishing-aware spam filters). He also managed to hijack his way into the web site of the French Consul General in London to host the bogus PayPal page and user ID/password gathering software. But English skills are definitely not his strong point.
Emergency! Everybody to ignore phishers!
Posted on December 23, 2007 at 10:35 AMDecember 16, 2007
One Sick 419er
Even if you think you've seen it all when it comes to tricks used by advance-fee (a.k.a. 419) fraudsters, one sick dude (or dudette) finds another way to sink several steps lower than what has come before. We've read the stories from cancer-riddled widows of deposed African ministers and we've won more lotteries than you can shake a stick at. Everybody simply can't wait to give us millions of dollars, euros, or pounds.
With so many 419 scams around the Internet—and the similarity of the pitches—the crooks try to make their initial offerings sound more legitimate. Why not commit fraud in the name of one of the most respected human rights organizations? Case in point:
AMNESTY INTERNATIONAL
Corso Ercole I d'Este 44,
Ferrara 44100 - Italy.Executive Secretary: John Nichole
Email: [removed]@yahoo.itFoundation's Officer,
Fondazion Di Amesty, ITALY
http://www.Amnesty.itIMPORTANT NOTICE/NOTIFICATION
The Foundazion di Amesty, would like to notify you that you have been Chosen by the board of trustees as one of the final recipients of a Cash Grant/Donation for your own personal, educational, and business Development.
To celebrate the 28th anniversary program, The Amnesty Foundation in conjunction with the Economic Community for West African States (ECOWAS),United Nations Organization (UNO) and the European Union (EU) is giving out a yearly donation of US$500, 000.00 (Five Hundred Thousand United States Dollars) to 100 lucky recipients. These specific Donations/Grants will be awarded to 100 lucky international recipients worldwide in different categories for their personal business development and enhancement of their educational plans. At least 15% of the awarded funds should be used by you to develop a part of your environment.
This is a yearly program, which is a measure of universal development strategy.You are required to fill the form below and email it to our Executive Secretary below for qualification documentation and processing of your claims. After contacting our office with the requested data, you will be given your donation pin number, which you will use in collecting the funds. Please endeavor to quote your Qualification numbers (N-222-6747, E-900-56) in all discussions.
FULL NAMES: __________________________________
ADDRESS: _____________________________________
CITY: _________________________
STATE: __________________________________
ZIP: ______________
COUNTRY________________________________
SEX: _______________
AGE: __________________
MARITAL STATUS: _________________
OCCUPATION: ________________________
E-MAIL ADDRESS: _____________________________
TELEPHONE NUMBER: _____________________===========================================
Executive Secretary: John Nichole
Email: [removed]@yahoo.itAll information is strictly confidential and will only be used for the
purpose to which it is been requested.On behalf of the Board kindly, accept our warmest congratulations.
Regards.
LADY RITA MOSLEY
(Foundation Officer)
The web site address supplied at the top of the message is the real Amnesty International site for Italy. I truly fear that those recipients who don't recognize this as a 419 scam will visit the site and deem this message to be legitimate. With bills from Christmas presents coming due next month, 500 grand would seem to come in handy.
Except that those who swallow the bait will be asked to fork over thousands of dollars for various processing fees and taxes...and then never see a dime.
I have a gleeful vision of this crook getting caught in, let's say, Nigeria and then being tossed into prison. The sad part is that Amnesty International would probably come to the prisoner's aid if he were being treated inhumanely. At least one party in the whole mess has a heart.
Posted on December 16, 2007 at 09:50 PMDecember 13, 2007
Replica Jewelry Spammers
I seem to get a lot of spam for replica watches, leather goods, and other knock-off products of high-end brands. At gift times, such as Christmas, the offers come pouring in left and right.
High-end brands spend a fortune trying to disrupt the flow of counterfeit goods, and I understand that. On the other hand, if you buy something that claims to be a Rolex watch from a sidewalk vendor for fifty bucks, you certainly can't have the expectation that the workmanship and materials are anything like a real Rolex (if there are any works inside the case at all). So much of the jewelry spam advertises the items plainly as replicas. Despite the fact that they are spamming—perhaps through an illegal botnet—you can't accuse them of false advertising.
But then, every once in awhile, you see a spam message like the one below, which is clearly trying to make the recipient believe it comes from none other than Tiffany & Co. (blocked characters shown as "+" symbols)
Date: Thu, 13 Dec 2007 22:05:58 -0800
From: "Tiffany Gifts" <order@tiffany+++++.com>
To: dannyg@dannyg.com
Subject: Christmas with Tiffany
Tiffancy & Co. Discount Retail Warehouse
One of the many last minute specials our Warehouse is currently offerring:
*Large Tiffany Bracelet Selection (#1 sellers this year!)
*Tiffany Earings
*Tiffany NecklacesShipping in-time for Christmas. Happy Holidays.
http://tiffany+++xmas.com/
Tiffancy & Co.© 2007.
When I first observed the message body, I was amazed that the spammer would tempt fate by tangling with Tiffany & Co.'s tradename, especially in the copyright notice. That was before I could "c" the difference between the company name in the message and the real company. Can you spot the other two misspellings in the body? Sometimes the eye sees what it wants to see.
BTW, the domain name for this counterfeiter's web site was so fresh, it didn't yet show up in the whois directory. The site is hosted...ta da!...in China.
I don't condone the practice, but if you're going to buy counterfeit luxury goods, do it off the back of a truck in a nearby alley. Don't respond to the spam, as it only encourages them to spam more. The spam, alas, is all too genuine.
Posted on December 13, 2007 at 11:10 PMDecember 12, 2007
eBay Phishing for High Value Accounts
I've been actively selling some items on eBay for the last couple of months. After years of accumulating "stuff," it's time to start simplifying. Prices have been all over the board, but one item that closed this evening would certainly be classified as a high-end item. It's the only item to which I had attached a reserve price just to make sure I wouldn't get too burned on it. I had received a few inquiries about the item via eBay's My Messages system. It's the only way an eBay seller or buyer should communicate with another party regarding a still-running auction because you need an eBay account to initiate a message.
A mistake that some eBayers must make is to use the My Messages mechanism that sends a copy of each incoming message to your regular account email address, and then respond using regular email. It's definitely convenient to get the messages in your inbox, because you're more likely to notice an inquiry that appears in your inbox than remembering to check your eBay account page every now and then. I, in fact, have the email copies sent to my inbox. But (and this "but" is bigger than my butt) I handle the reading and responding of such messages solely on the eBay site that I have bookmarked. This is to prevent a phisher from slipping a lookalike message into my email inbox without using the eBay mail system.
However...
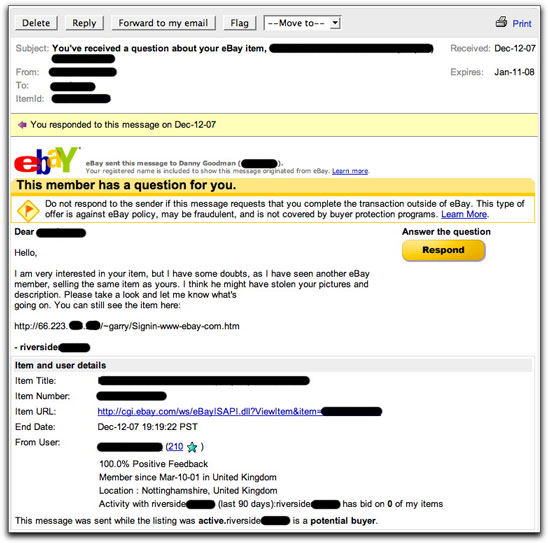
The crooks are also using the eBay mail system to phish for accounts. A few hours before the end of my high-value item auction, I received a message via the genuine eBay My Messages system, as shown here:
As I explain in detail in my EMail Safety 101 Course, spammers and scammers entice recipients to perform one of several actions, any of which will benefit the sender to the detriment of the recipient. The come-on with this message was some "good samaritan" alerting me to the possibility that someone had hijacked my high-value item photos for a bogus auction. He was, in a sense, challenging the authenticity of my auction because he had supposedly seen identical photos elsewhere. I could look at the other auction by visiting the URL in the message.
As you can see, the URL starts with a numeric IP address, rather than "ebay.com." If I had visited that address with a web browser (which I did not do—I just safely viewed the source code), I would have seen a phony eBay login page, requesting my username and password. The results of that form would have been relayed via email to a Google mail account (to a username that references a Central American criminal gang no less).
If I had supplied the login information, my eBay account would have been quickly hijacked, leading to the auction winner ultimately putting funds into the crook's hands through a couple of means. The easiest way would be for the crook to suddenly come up with a new way to pay (concocting some outrageous story that would force the buyer to pay using Western Union, I presume). More crookedly, he would try to use the same eBay login credentials to access my PayPal account so that the buyer could transfer funds normally, but I would not be able to get the money—the crook would change the password to lock me out, and then do whatever it takes to get the funds sent his way. (This, by the way, is reason enough to have different login credentials for linked accounts, such as the eBay/PayPal combination—if one account gets compromised, the other doesn't necessarily follow.)
You may wonder how the original eBay message system was able to convey this phishing message to me. I can only assume that the crook was using a previously compromised (i.e., phished) account to send the message. Heaven knows what other kinds of auction fraud he is perpetrating with that account.
I'll bet this jerk was mightily pissed off when he not only didn't get my login credentials, but the auction zoomed past my reserve price in the final minutes. "No soup for you!"
(Incidentally, because this is such a high-value auction and I have not dealt with the winning buyer before, my Suspicion Radar is set to maximum gain. I am aware of most auction payment scams, so I don't yet consider this auction to be a done deal.)
After alerting eBay to the spoof and hijacked account, as well as notifying the owner of the hijacked Canadian web site being used to host the phony login page, I used the eBay My Messages system to respond to the message:
Go peddle your phish elsewhere.
UPDATE (13December2007): A little more than 24 hours after my report to eBay, I received a form letter advising me that any message I have received from that eBay account may be fraudulent. Duh. Unfortunately, the account is still showing up as active. It can be frustrating to get large companies such as eBay to act quickly on what is obvious fraudulent activity.
Posted on December 12, 2007 at 08:47 PMDecember 08, 2007
Wrong on So Many Levels
An author of 45 books is, by nature, a bibliophile (lover of books). I can't help it. When I was in the Eisenhower-era third or fourth grade, my elementary school belonged to a program that let students buy books (not the textbooks) right in the classroom—probably some program that a publisher or distributor sold to the school district to provide kickbacks to the district (ah, the cynicism of middle-to-old age). I don't remember much about the selections (the catalog must have been well-sanitized for our protection), but those rare days when the books arrived were my happiest days of the otherwise desperately long school year.
Thus, the Subject: line in my email program's Spam folder peaked my curiosity:
New amazing shopping place for books [removed].com
I didn't recognize the domain name at all. It sounded like something in a foreign language, perhaps from South Asia. For a reason I'll never be able to fathom, I am on a lot of Malaysian spam lists, and the domain name for this spam sounded as though it could have been from there.
First things first. I opened the source code view of the message to look for any signs of nastiness, even though my email client is theoretically immune to the usual "phone home" and auto-download shenanigans. You can't be too careful these days.
The message was in plain text, so there was no HTML malarkey going on. But the content...well, I think I'd expect a bit more literacy from a bookseller:
HelloThe newest shopping place just start to work and we invite You to look us site. There You can bargain for the lowest price ever. Books aprox. for 4$ and lower. You must see that .
administration
www.[removed].com
This message is sent using [Removed] Server Professional Trial:
http://www.[removed].com/
Not wanting to assist this spammer in any way—including registering a hit on his web site—I started a typical investigation trail. I began with the domain registration. The identity was blocked through one of those domain cloaking services. For a commercial endeavor, that can't be a good sign. To his partial credit, the domain was registered in February of 2007, so it wasn't born yesterday.
Next I went to Google to see if the domain name (thankfully uncommon) garnered any hits elsewhere. I found a few listings that appeared to be affiliate sites ("buy 9 get 5 free" appeared in the Google summary), as well as several blog spam hits with links to the main site. Ugh, this was going to be painful. The main site, itself, showed up in Google's listing. Fortunately, Google had a cached copy of the page, which would allow me to view the home page without registering a hit with the actual site. Cool.
But before I would even do that, I bore in mind that Google has been linking to pages that have contained malware. Although Google has been working to clean that up, the fact a) that my invitation to the site came via spam, b) that the domain name record is cloaked, and c) that they use blog spam made me more than cautious. To be on the safe side, I viewed the HTML source code of the cached copy on the Mac's text-only Terminal program (using the curl command). I agree, it's like wearing two hazmat suits to clean up a spilled glass of milk, but I didn't want to give this spammer any chance of benefiting from his emission.
I saw no malware loading on the page, but there was a hit counter on another domain. Checking only the HTML source code prevented the hit counter from counting. Yay!
Based on what I read in the HTML source code (horribly coded, by the way), this site sells ebooks. It's not painfully clear from the home page because aside from being garbled English (no better than the spam message), details about what they do are few and far between. But links on the home page to download WinZip and Adobe Acrobat are dead giveaways.
With a bit more careful digging, I found a very long list of computer books this outfit offers (under "Business," go figure). My books get pirated quite a bit, especially the editions that come with a CD-ROM containing the PDF version of the book. It takes zero effort on the part of a pirate to compress the file and put it up on RapidShare and elsewhere for free download. My publishers' legal departments have staff whose jobs are to find these pirated copies and get them taken down. It was no surprise to find some of my books on the list.
Here's where it gets a bit interesting. Two editions of my JavaScript Bible appear on the list. Both editions (which were released in 2001—it's a long, boring story) are two editions earlier than the current 6th edition. We're talkin' Olde Schoole. But this "amazing shopping place for books" is charging money for these old ebooks. As partly described in the spam message, the sales premise for this "bookstore" is that interested buyers make an offer on however many titles they're interested in. There is no listed price per title, although the email message suggests prices are $4 or lower. Payment is made through PayPal and Skype Pay.
In looking through the rest of the list and other categories, I sensed that this list was awfully familiar. If I'm not mistaken, the inventory source for this "amazing shopping place for books" was a DVD available a few years ago that contained all of these titles already. The disc used to be offered on eBay (especially in the U.K.) for dirt cheap (like ten pounds for the entire collection). I had dozens of those auctions taken down. Some of the sellers then took my title off the displayed lists of titles, although I'm sure the books were still on the discs. I also alerted my publishers and author friends to pursue the same action whenever these unauthorized ebooks appeared on auction.
And so, we have a spammer trying to sell for real money pirated electronic copies of very outdated books (most already available for free download with a little digging) to unsuspecting suckers. It wouldn't surprise me if this spammer didn't buy a kind of kit containing the DVD and instructions how to spam using a free copy of the [Removed] Server software—all in an effort to start his own Internet business. If that's the case, I suspect that the only party who makes money on this deal is the guy selling the kit and the promise of Internet Riches.
The capper is that this spamvertiser of pirated property has the gall—no, the balls—to plaster a copyright notice at the bottom of his ugly-ass web site pages. All Rights Reserved. He can't possibly know what that means.
As for the true identity of this spammer, it's hard to say. The server software referenced in the message lets you essentially install an outgoing email server on your PC, allowing you to send email without going through your ISP's outgoing server. That's how computers that are members of a botnet convey their messages to escape being quantity-limited by an ISP's server. (I'm not saying that this particular server software isn't a legitimate program, but its mechanism appears to be the same as that used by zombies.) That the tagline appears in the spam message means that the spammer has outlasted the software's trial period, and doesn't appear to be ready to pay for it (surprise, surprise!).
The computer that sent the message was located not in South Asia, but in Lithuania, as likely as any place for this spammer to be waiting to Get Rich Quick on the Internet. I'll have to drop him a note and tell him to make sure he sends me my royalty checks.
Posted on December 08, 2007 at 10:56 AMDecember 07, 2007
"Does Anyone Fall for Lottery Scams?" You Ask
According to my list of server-deleted email, I must be the luckiest guy on the planet. I win so many online lotteries (despite having never entered) that I am an utter fool for slogging away daily on my computers and making mortgage payments.
Back in May, instead of deleting all my incoming spam, I captured one day's worth to gather in-the-wild examples for my Email Safety 101 course. On that particular day (chosen completely at random), I had won no fewer than three lotteries for a total of over four million currency units (dollars or euros).
Everyone reading this blog, of course, knows better. But there are still tons of email users out there who don't. Case in point: A Lebanese man was arrested recently for having allegedly scammed $10 million from lottery "winners." (The Register story here) Now there's a guy—until nabbed by police, that is—who really won the lottery.
Reaching potential victims of this and other scams is by far the most difficult task facing spam/scam fighters today. What are you doing to spread the word to those most at risk?
Posted on December 07, 2007 at 08:25 AMDecember 03, 2007
Medz Sunday
If you follow my Spam Stats charts on a regular basis, you've certainly observed the pattern of lower overall volume on weekends compared to weekdays. Thus my surprise to see Sunday, December 2, 2007 showing up with a hefty spike in regular spam activity (not dictionary attacks, which can occur on any day). Curious about what might trigger such a rush, I checked the logs of Subject: lines of the server-deleted messages.
A vast majority of the volume appears to have been selling various prescription medicines—or medz, as I call the spammed variety (whose actual medicinal contents are questionable). Pain and anxiety were the main targets (Vicodin, Hydrocodon, Valium), with sleep (Ambien) and weight loss (Phentermine) next in line.
(Damn! I also saw that an Internet millionaire was giving away his business plan, but the message got deleted.)
Here in the U.S., the news media have created nicknames for a couple of pre-Christmas shopping days: Black Friday for the day after Thanksgiving; Blue Monday for the following Monday when Internet shopping supposedly spikes. I wonder if this first Sunday of December deserves its own such designation based on the amount of spam that suddenly flowed across the wires. But what color? Pills come in all kinds of tasty-looking colors. Black is already taken. Then it occurred to me: Based on the apparently uncontrollable spew of medz spam, the spammers could use a sizable dose of Immodium. I think I'll call it Brown Sunday.