| Home | The Book | Training | Events | Tools | Stats |
March 26, 2012
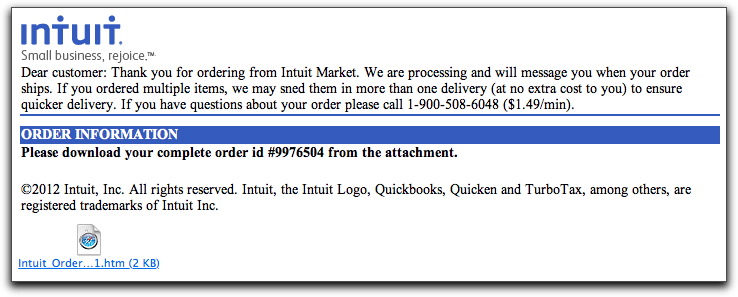
Faux Intuit Malware Lure
This one is just another variation of the fake IRS email previously reported here. Instead of invoking the IRS, it claims to be an order confirmation from Intuit, to wit:
The attached HTML file is similar to the one discussed in the fake IRS message, whereby you'll see a "Loading. Please wait." message while a bunch of obfuscated JavaScript is executed to direct your browser to more harmful pages.
Posted on March 26, 2012 at 04:34 PMMarch 21, 2012
Faux IRS and PayPal Messages Spreading Malware
Both of the social engineering tricks shown in the following email examples try to raise the adrenalin of the recipient with the hope that the rush causes immediate clicking or opening. Both involve money (surprise!), either that you are made to think you won't get back (IRS refund) or had lifted from your account (PayPal).
First the fake Internal Revenue Service notification. The Subject: line reads "Your tax return appeal is declined." Then comes the message body that includes logos directly from the irs.gov web site, but in a silly arrangement that makes the IRS look like it's creating a doorbusting sale advertisement:
The payload is an attached HTML file, which, when decoded, reveals a good amount of obfuscated JavaScript — a sure sign that the sender is up to no good. If you were to open the attachment, you would see momentarily the wording
Loading. Please wait.
That gives you something to look at while the script determines if you are running a susceptible operating system/browser. If your computer qualifies, let the malware loading begin!
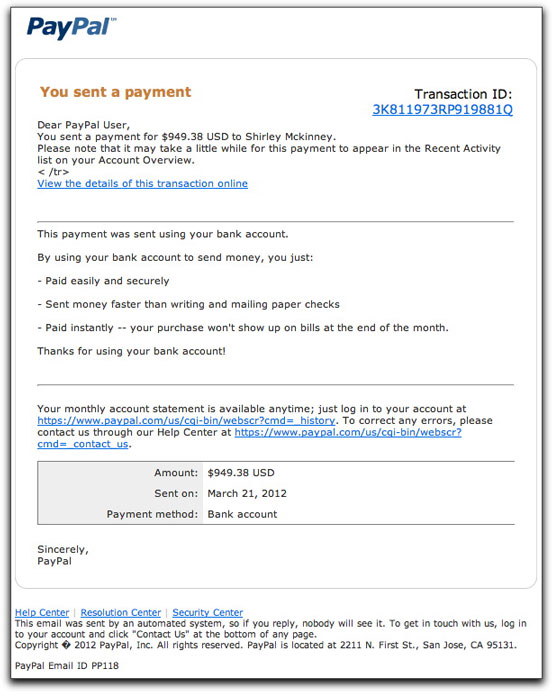
Today's PayPal-inspired malware missives look halfway decent (except for the errant HTML end tag).
If you receive multiple messages, they'll likely have different dollar amounts and names of people to whom money was(n't) sent. Each of the seven links in the message goes to a different hijacked web site, where the multiple-copy JavaScript loading gimmick reported here takes over. While that's doing its stuff (redirecting and script-checking your system), you see momentarily the following in your browser:
WAIT PLEASE
Loading...
This observable behavior makes me think the campaigns are related, perhaps by authorship.
Although most of these types of JavaScript-in-an-HTML-document attacks have targeted unpatched Windows PCs in the past, I get more nervous about them than .exe or similar executable attachment. While executables are more easily spotted in an email attachment, you just don't know what a JavaScript-based attack is doing unless you painstakingly fetch the script code (not in a browser) and study it, often requiring careful examination to inhibit code that is booby trapped to execute when being studied. A script-based attack could silently afflict systems other than Windows, should the crook know how to take advantage of an unpatched or zero-day vulnerability. Even though I'm primarily a Mac user, I don't feel that my systems are untouchable. Mac and Linux users can just as easily fly too close to the Sun with their wax wings.
Posted on March 21, 2012 at 10:15 AMMarch 16, 2012
You Have NOT Won an iPad 2 [or 3]
Look at this bullshit:
From: Apple® <iPad3request@apple.com> Subject: deal or no deal
These fraudsters are also kind of stupid. To broadcast a bogus offer for the iPad 2 on the release day of the succeeding generation is idiotic at best. I mean, if you're going to hold out a fake carrot, at least make it a good one.
[Update: Apparently the crook has updated the artwork to say "iPad 3", which is equally ludicrous.]
It's clear the sender hopes recipients believe this offer comes from Apple, and a simple click is all you need to finish the job. What isn't clear is that the link is to a domain whose name includes the word "timeshare". That page redirects to another domain that wraps you up into a barrage of surveys (for which the host makes money) and other costly tricks that aren't worth the effort (and usually entail giving up the email addresses of your friends in the process).
Forging the headers, as this message does, is enough for them to be prosecuted for CANSPAM violations. But that assumes the crooks behind this scheme are in the U.S., which I doubt. In any case, don't fall for it. Don't even click the link to satisfy your curiosity because the links might be coded to verify your email address.
Posted on March 16, 2012 at 07:11 PM
Yet another attempt to trick unsuspecting victims. This one comes in the form of a bogus alert from Bank of America suggesting that you wired a big chunk of dough to an international recipient. Here's one version of the message I've seen:
From: Online Transfers from Bank of America
Subject: Your Same Day wire transfer was successfully sent
We have successfully sent the following transfer:
*********************************************
Item #: 996474891
Amount: $5151.00
To: Brooks Sports
Fee: 45.00
Send on Date: 03/16/2012
Service: International
*********************************************You can always check your transfer status on the Review Transfer screen at www.bankofamerica.com.
Wire Details Report: report_996474891.doc (Microsoft Word Document)
Sincerely,
Member Service
www.bankofamerica.com
(C) 2012 Bank of America Corporation. All rights reserved.
The links are to a hijacked Turkish web site, where the inserted page loads not one, not two, but five copies of the same JavaScript script, each one hosted at a different domain or IP address. The script loads a page from a still different hijacked web site.
Although phony banking alerts typically lead to phishing pages, there are hallmarks of this campaign that point more to malware delivery. Of course, one cybercrook is equally capable of pulling off both types of scams. Installing malware helps build the bot network; phishing helps fund the botnet-building activity.
In any case, I can see recipients of this message (who are also Bank of America customers) freaking out about a $5100 wire transfer. If you want to put your mind to rest about this possible transaction, ignore the links in the message and log into your BofA account by way of the bookmark you normally use to do your electronic banking. Any wire transfer would show up as a debit in your account — but you will find no such debit because this email is entirely bogus.
Posted on March 16, 2012 at 11:00 AMMarch 13, 2012
I'm in Trouble! (Not!)
Doofus malware spreaders are at it again. Today's incoming had lots of messages like the following:
Subject: I'm in trouble!
I was at a party yesterday, got drunk, couldn't drive the car, somebody gave me a lift on my car, and crossed on the red light!
I've just got the pictures, maybe you know him???I have attached the photo to the mail (Open with Internet Explorer).
I need to find him urgently!
Thank you
Zenith
The real trouble is that the crook didn't program his malware-sending bots to change out the From: header lines from previous campaigns. We had suffered many days of the "we can't deliver your package" spam containing malware attachments. He changed out the Subject: and message body, but the From: fields are from the old campaign:
From: package update <ups-account-services@ups.com>
From: UPS <ups-services@ups.com>
If the story in the message sounds familiar, well, it should. Open an attachment/click a link — they all lead to the same bad end.
Posted on March 13, 2012 at 10:54 AMMarch 02, 2012
FBI/ATM 419er Keeps Deadbeats at Bay
An advance-fee scammer's email claiming to be from FBI DIRECTOR (with an aol.com email address -- haw haw) makes me wonder what fantasies whirl through the minds of these crooks. The stories they invent often defy logic, but I guess those who fall for these tricks ignore the disconnected dots on the way to a supposed multimillion dollar payday.
Today's example uses up a lot of 419 material. It starts out with a threat that the recipient is engaged in illegal activity (including the first time I've seen them refer explicitly to puppy scammers). Suddenly they shift gears to tell the potential victim of a massive "Contract / Inheritance payment" (that covers the gist of a lot of long-winded, non-lottery 419 scams) of $11 million...in the form of an ATM card that needs to be claimed.
Next they show the names and UPS or FedEx tracking numbers of previous payment recipients. I referred to these tracking numbers in earlier posts, and unfortunately, the ones in this email are real tracking numbers for deliveries to various U.S. towns. Only one record showed the origination point of a shipment, in Pennsylvania. I strongly doubt the crooks had anything to do with those shipments, perhaps entering random numbers into the tracking services to find real ones to use in their email messages.
As has been happening in several 419 scams of the ATM card variety recently, this one reveals up front that the victim needs to wire $255 for the card to be shipped. The victim is to believe that "there is no other payment attached to this after the payment for your delivery has been confirmed." If you believe that, I have a beautiful red bridge spanning the Golden Gate I'd like to sell you.
I must say that the part of this message that tickled me the most is the following: "please if you know you cannot be able to afford the US$255 for the shipment of your ATM card, then do not bother to contact Mr. Frank Diru for your ATM card shipment." That's right: Don't unload your poverty sob story onto the crook. He doesn't want to hear it.
And now, for your coffee break enjoyment, the full text:
Attn: Beneficiary,Posted on March 02, 2012 at 11:04 AM
This is to officially inform you that it has come to our notice and we have thoroughly investigated with the help of our Intelligence Monitoring Network System that you are having an illegal transaction with impostors claiming to be Prof. Charles C. Soludo of the Central Bank Of Nigeria, Mr. Kelvin Williams, Zenith Banks, Mr. Michell Brown From union bank, kelvin Young of HSBC, Ben of FedEx,Ibrahim Sule,Larry Christopher, puppy scammers are impostors claiming to be the Federal Bureau Of Investigation.
During our Investigation, we noticed that the reason why you have not received your payment is because you have not fulfilled your financial obligation given to you in respect of your Contract / Inheritance payment, and also the wrong people that you have been dealing with earlier.
Therefore, we have contacted the Federal Ministry Of Finance on your behalf and they have brought a solution to your problem by coordinating your payment in total US$11million in an ATM CARD which you can use to withdraw money from any ATM MACHINE CENTER anywhere in the world with a maximum of US$5,000 per daily withdrawal.
Below are few list of tracking numbers you can track from FedEx website to confirm people like you who have received their payment successfully.Name: Donna L. Vargas: UPS Tracking Number: 1Z966AR90105033136 (www.ups.com)
Name: Rovenda Elaine Clayton: UPS Tracking Number: 1ZA0T5861379047617 (www.ups.com)
Name: Linda Emlina: FedEx Tracking Number: 468888861983 (www.fedex.com)
Name: Susan T. Love: FedEx Tracking Number: 949856926109095 (www.fedex.com)
You now have the lawful right to claim your fund in an ATM CARD. Since the Federal Bureau of Investigation is involved in this transaction, you have to be rest assured for this is 100% risk free it is our duty to protect the lifes. All i want you to do is to contact the ATM CARD CENTER via email for their requirements to proceed for the delivery of your ATM card, and it will cost you US$255 only and note that without this payment your ATM card cannot be delivered to your doorstep.
This is the only payment legally requested of you to do for ATM CARD, to be delivered to you safely. there is no other payment attached to this after the payment for your delivery has been confirmed.
After the your payment has been confirmed by the courier company your ATM card will get to your doorstep within 24hrs, this was the assurance giving to the us by them, and it was officially signed by the fedex courier manager. And after your package leaves for a tracking number will be giving to you, where you can track your package in their website http://fedex.com/ng/
CONTACT INFORMATION, ATM PAYMENT CENTER:
NAME: Mr. Frank Diru
Address: 86b Peterson Close Off Moblie Road Apapa Lagos
EMAIL: xxxxxdiru@yahoo.cn
Telephone:+234-815-xxx-xxxx
Do contact Mr. Frank Diru with your correct details, to avoid mistake during delivery:
FULL NAME:
HOME ADDRESS:
TELL:
CELL:
CURRENT OCCUPATION:
GENDER/ AGE:
So your files would be updated after which he will send the payment information which you will use in making payment of $255 via (WESTERN UNION TRANSFER) or (MONEY GRAM TRANSFER) for the procurement of your APPROVAL SLIP after which the delivery of your ATM CARD will be effected to your designated home address without any further delay.
You are advice to call him with his number +234-815-xxx-xxxx before sending him e-mail and please if you know you cannot be able to afford the US$255 for the shipment of your ATM card, then do not bother to contact Mr. Frank Diru for your ATM card shipment.
Note: Do disregard any email you get from any impostors or offices claiming to be in possession of your ATM CARD, you are hereby advise only to be in contact with Mr. Frank Diru of the ATM payment center who is the rightful person to deal with in regards to your ATM CARD PAYMENT and forward any emails you get from impostors to him so we could act upon and commence investigation.