« You Have NOT Won an iPad 2 [or 3] | Main | Faux Intuit Malware Lure »
| Home | The Book | Training | Events | Tools | Stats |
March 21, 2012
Faux IRS and PayPal Messages Spreading MalwareBoth of the social engineering tricks shown in the following email examples try to raise the adrenalin of the recipient with the hope that the rush causes immediate clicking or opening. Both involve money (surprise!), either that you are made to think you won't get back (IRS refund) or had lifted from your account (PayPal).
First the fake Internal Revenue Service notification. The Subject: line reads "Your tax return appeal is declined." Then comes the message body that includes logos directly from the irs.gov web site, but in a silly arrangement that makes the IRS look like it's creating a doorbusting sale advertisement:
The payload is an attached HTML file, which, when decoded, reveals a good amount of obfuscated JavaScript — a sure sign that the sender is up to no good. If you were to open the attachment, you would see momentarily the wording
Loading. Please wait.
That gives you something to look at while the script determines if you are running a susceptible operating system/browser. If your computer qualifies, let the malware loading begin!
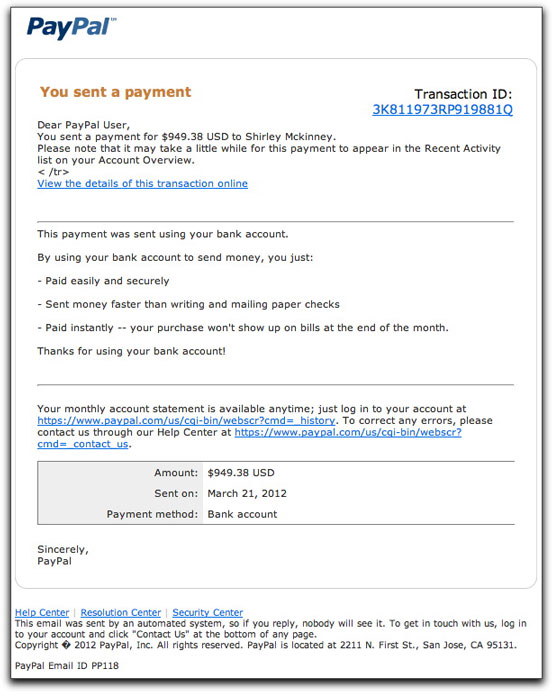
Today's PayPal-inspired malware missives look halfway decent (except for the errant HTML end tag).
If you receive multiple messages, they'll likely have different dollar amounts and names of people to whom money was(n't) sent. Each of the seven links in the message goes to a different hijacked web site, where the multiple-copy JavaScript loading gimmick reported here takes over. While that's doing its stuff (redirecting and script-checking your system), you see momentarily the following in your browser:
WAIT PLEASE
Loading...
This observable behavior makes me think the campaigns are related, perhaps by authorship.
Although most of these types of JavaScript-in-an-HTML-document attacks have targeted unpatched Windows PCs in the past, I get more nervous about them than .exe or similar executable attachment. While executables are more easily spotted in an email attachment, you just don't know what a JavaScript-based attack is doing unless you painstakingly fetch the script code (not in a browser) and study it, often requiring careful examination to inhibit code that is booby trapped to execute when being studied. A script-based attack could silently afflict systems other than Windows, should the crook know how to take advantage of an unpatched or zero-day vulnerability. Even though I'm primarily a Mac user, I don't feel that my systems are untouchable. Mac and Linux users can just as easily fly too close to the Sun with their wax wings.
Posted on March 21, 2012 at 10:15 AM