| Home | The Book | Training | Events | Tools | Stats |
September 21, 2010
Facebook Malware Ruse
Facebook gets abused regularly in one way or another as a vehicle to get the attention of unsuspecting users. It's a popular service, so when a message purports to come from Facebook and involves passwords, recipients pay attention. Perhaps too much attention:
Subject: New Facebook password!Dear user of facebook.
Because of the measures taken to provide safety to our clients, your password has been changed.
You can find your new password in attached document.
Thanks,
Your Facebook.
The attachment (named New_Password_Nr57012.zip in the copy I saw) has a very low antivirus detection rate according to VirusTotal. Coverage will certainly improve over the next hours, but in the meantime, lots of misguided trusting users will get blitzed.
September 17, 2010
Another Round of Tricks
I've written before about one particular botnet spammer who tries a variety of social engineering tricks to entice spam recipients to act — click a link, open an attachment, etc. It's the same guys I wrote about last month with their bogus LinkedIn spam. Those messages contained a link to a page named x.html at a hijacked web site. From there, the visitor was treated to a variety of malware loading and/or Canadian Pharmacy advertising (or both). The meta refresh URL this time hints at the site being a fake antivirus site (the kind of page that tries to make visitors believe their PCs are infected, and then try to sell the solution -- which just installs more malware on the PC).
Today, it's the same destination, but a different tactic. You see, in the previous LinkedIn version, the lure was a phony invitation from someone who claimed to know you — but you couldn't possibly know the random person used in the email. Today's version uses a different approach: at least three (that I've seen...but probably more) appeals to entice you to open a tiny (896 bytes) HTML attachment. The message texts read as follows:
Subject: Randolph PlansThank you very much for meeting with me on Saturday. Attached are the plans for the Randolph Street Development project we discussed. If you have any questions please don't hesitate to contact me.
Thanks again.--
[attachment named 25004Randolph - Revised plans.html]
Subject: credit cardDear all:
Have you used credit card as per attachment?
If you had used it, please provide the purpose and supporting paper.
Thanks
[attachment named 9730811.html]
Subject: A very warm invitation to youHello,
Hope your week has been wonderfull well. I would like to extend a very warm invitation to you to the Verbum Dei Missionary Festival this Sunday, September 19.
With a lot of support and collaboration from groups of people we work with in the Bay Area, an international spread of food
will be served at the festival. Besides the spread, cultural and folkloric performances, music, games for children, and activities will be part of the day's programme.
This once a year event brings all of our friends and family from around the Bay Area, an expression of the internationality of our community, mission and work here. At the same time, the festival is also a fund-raising initiative open to all, which is important for us in the ongoing Verbum Dei mission here in the Bay Area.
I really look forward to your coming to be able to catch up more. More details are in the attached invitation, I hope the directions woul be helpful in navigating the way to the St. Thomas More parish.
With joy and peace to you,
Garth Pool[attachment named 97445Verbum_Dei_Missionary_Festival_2010.html]
Decoding the Base64 HTML attachment you'd find merely a <script> tag that contains further obfuscated JavaScript. If you're not smart about dealing with this stuff, and simply copy/paste the decoded (but still obfuscated) script into a test page, you'd accidentally visit the destination page. But I saw their trap ahead of time, and was able to capture the URL. As readers know, I refuse to visit spamvertised URLs (even safely) when the URL contains anything that looks like an affiliate identifier to prevent anyone from making a fraction of a penny from me. This URL was not affiliate-encoded.
But the URL had a familiar trademark: the x.html page. I expected that page to be similar to the LinkedIn campaign, and upon inspecting the contents (not in a browser), I was not disappointed. There was a hidden iframe to one site and a meta refresh tag to another site (with an affiliate ID and a delay of four seconds...presumably to give the hidden iframe time to do its dirty malware work).
For everyday email users, the common denominator for these — and all other — malware/spam campaigns is the fact that the perps do everything in their power to get you to act, even if it's just to click or double-click on something. Clicking is just so easy...and the Web is so much fun because you never know what you'll find at the other end of a link. If only recipients would treat unknown senders as strangers with candy....
Posted on September 17, 2010 at 08:24 AMSeptember 03, 2010
Slop(py), Thief!
Everyone loves a tax refund, but one credit card thief isn't very clever (or good at the English language). He begins by identifying his From: address as 3D Secure, whatever that is. Here's the rest of the message:
Subject: Tax refund notification!You have get a Tax Refund on your Visa or MasterCard.
Complete the formular, and get your Tax Refund.(Your Refund Amount Is $620.50)
Complete Formular
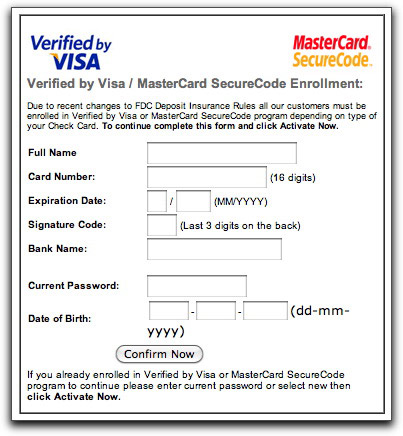
The link leads to a highjacked Korean web site, whose BBS icon directory is hosting an HTML page consisting entirely of obfuscated JavaScript. When the script executes upon loading, it replaces itself with an HTML page with nothing more than the following form:
If anyone is foolish enough to fill out the form and click the button (instructions call it "Activate Now," but the button is labeled "Confirm Now"), the data is sent to a server program on yet a different Korean web site. Then it's only a matter of time before another crook buys the number and uses it for an online purchase or makes a fake magnetic strip to try out the number on a gas pump.
Posted on September 03, 2010 at 03:37 PMSeptember 02, 2010
You've got a fax ... NOT!
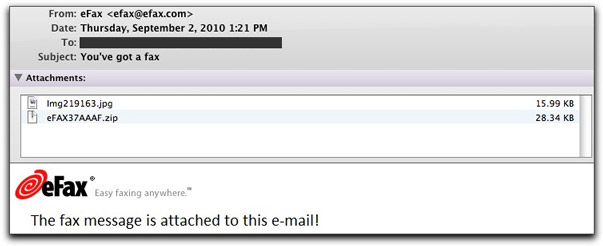
Malware spreaders will do anything to make their spam recipients do something unhealthy for their computers, privacy, and security. Foisting an email message claiming to come from a FAX service (efax.com, a legitimate company being abused by the bad guys) on unsuspecting victims will get plenty of them to open the attachment — which has a 37% detection rate on VirusTotal.
Here's what one of today's messages looks like:
One attachment is the image that you see in the message body. The other is a Trojan, identified by antivirus products as one of several possibilities. It doesn't really matter which specific malware type it is. Once a machine is infected with one type of malware, the PC can be repurposed for other bad things at will (and behind the scenes).
If you're a Windows user, and you open this particular attachment, you don't have a FAX, but you do have a big problem.
Posted on September 02, 2010 at 02:00 PM