| Home | The Book | Training | Events | Tools | Stats |
June 30, 2009
More on the URL Shorteners
Not all URL shorteners are created equal when it comes to handling abuse complaints. Yesterday's flood continues. I went back to see how my abuse reports faired. Of the services I contacted, the only one that seems truly diligent about stomping out spam abuse of their service is is.gd. Four gold stars for them!
The one that looks to be the most problematic is kl.am, which appears to be run by a Tennessee "online marketing" firm called Sitening LLC. Unlike the responsive shorteners, kl.am does not have an abuse reporting link on their main page...or anywhere. Moreover, the main page is titled:
Shorten URL with URL Shortener for Internet Marketers
In other words, they seem to be encouraging the use of URL shorteners by commercial emailers. What a great way for a company to build an online brand presence—by hiding behind a URL shortener. WTF?
OTOH, it makes it easy for me to handle any company that takes advantage of this shortening service for spam purposes. From hereon, any email message body that contains a kl.am URL arriving from a non-whitelisted address goes straight to dev/null. See y'all!
(Tinyurl may be next.)
Posted on June 30, 2009 at 08:15 AMJune 29, 2009
URL Shorteners in Spam
Some "business opportunity" spammer has been flooding the intertubes with brief messages that use just about every URL shortening service on the planet, including several I had never before heard. Here is a sample of the source code of one of them sent from a pwned PC in Brazil (identifying bits [removed] or xx'd):
Received: from 189-19-xx-xxx.dsl.telesp.net.br (189-19-xx-xxx.dsl.telesp.net.br [189.19.xx.xxx]) by dannyg.com (8.12.11.20060614) id n5TEwPrW040161 for <[removed]@dannyg.com>; Mon, 29 Jun 2009 08:58:26 -0600 (MDT)
Message-ID: <4A48D688.1018475@{$FROMDOMAIN$}>
Date: Mon, 29 Jun 2009 14:58:16 GMT From: Stephanie <StephanieLoyd36@{$FROMDOMAIN$}>
User-Agent: Thunderbird 2.0.0.12 (Windows/20080213)
MIME-Version: 1.0
To: <[removed]@dannyg.com>
Subject: Online Jobs : The Next Goldrush?
Content-Type: text/plain
Content-Transfer-Encoding: 7bit
X-UIDL: 2&j!!~ai"!RaD!!)[8"!
Someone wants to share this news article with you:
http://xx.xx/11ZkUser Comment:
im pretty motivated after seeing this..what do you think?Source: The Business News
I've filed half a dozen abuse complaints to the URL shortening services in the last 12 hours in the hope that the offending URLs will be shut down quickly. Of the shortening service Terms of Service that I've read, none of them permit using their domains as spam destination halfway houses.
Note, by the way, how the botnet software fails to mail merge a bogus domain name into the Message-ID: and From: header field placeholders.
The shortened URLs lead to a domain that claims to be registered by someone in China and has been alive for about a week. Ah, if only China would shift its internet blockage infrastructure into reverse....
So, I guess I'll keep playing whack-a-mole until one of us gets bored. Hint:it won't be me.
Posted on June 29, 2009 at 08:30 AMJune 28, 2009
Item Followups
I'm going to combine updates of two different items in this posting. One is kinda funny, the other not at all. I'll deal with the unfunny one first.
In yesterday's post, I talked about a malware-looking ecard spam message that led to a medz spamming page. The campaign continues, but the URLs are now leading to an executable PC file (.exe) that is pure malware.
What interests me most about this is that for the past few years, I've seen plenty of evidence that the originators of many malware lures and the so-called Canadian Pharmacy medz (and other) spam are one in the same. "They" mail to the same lists (which include some of my spamtrap addresses), and there is a similarity to their campaign tactics. I think the medz link in yesterday's email was a glitch in their system, and it only added more to the argument that this medz/sex/knockoffs spam gang is actively involved in building botnets and stealing private information (e.g., trojans that steal password credentials).
I'd like to think that if those who buy from the spammers knew they were funding malware development and distribution activity, they'd think twice. But that's like saying a heroin addict who learns where poppy plants are grown would care about funding the Taliban.
For part two of this update, I remind you of the posting about a 419er who exposes 400 email addresses in his "You've won an award!" spam. I just saw a spam message from a 419er who indavertently acknowledges he's not smart enough to figure out how to disguise recipient email addresses as blind copies (BCC). But he is aware that the To: addresses are open for viewing:
From: MARSHALL CHI
Subject: HI
the nigeria government is given $35,million us$ contract payment for
2010 africa world cup to 80 lucky people, all the 80 emails are will
shown please cross check to see if you can see your email if you do
please kindly fill this form below.1, your full name
2, your phone number
3, your country
4, your sex
5, your age
6, your home address
7, your occupation
8, your international passportplease reply to this email address below
[removed]@hotmail.com
Isn't it odd that the 80 lucky people all have email addresses that start with the same two letters? This guy has a way to go before he understands how to send his blocks of spam to a randomized list of rented addresses if he intends to expose them. Oh, and he also needs to learn how to count because the contiguous block of addresses in the message I received contained 90 addresses, not 80.
Bad 419er! Go sit in the corner.
June 27, 2009
How to Piss Off Your Potential Customers
If you've ever read much about marketing, you've probably heard the expression "underpromise and overdeliver" as a way to impress customers with more than they thought they'd receive. I just saw a spam message that exercises a corollary to that old expression: "overpromise and deliver squat."
Here's the message:
Subject: You've received a greeting ecardGood day.
You have received an eCardTo pick up your eCard, choose from any of the following options:
Click on the following link (or copy & paste it into your web browser):http://[removed]view.com/
Your card will be aviailable for pick-up beginning for the next 30 days.
Please be sure to view your eCard before the days are up!We hope you enjoy you eCard.
Thank You!
If you've been monitoring the spam business as long as I have, the first conclusion jump is that the destination URL is a drive-by malware installation web site. Seen it a gazillion times before.
But if you're an unsuspecting email user, you likely believe that there is an ecard from an unknown admirer at the end of that link. Oh, goody goody!
You click.
And what do you see? Why none other than the spam defender's worst nightmare:
So much for your secret admirer. Buy some fake Viagra instead.
I may not be the world's best businessperson, but I know enough not to aggravate your customers when they come through the door and make them feel like stupid asses for having entered.
Posted on June 27, 2009 at 01:36 PMJune 22, 2009
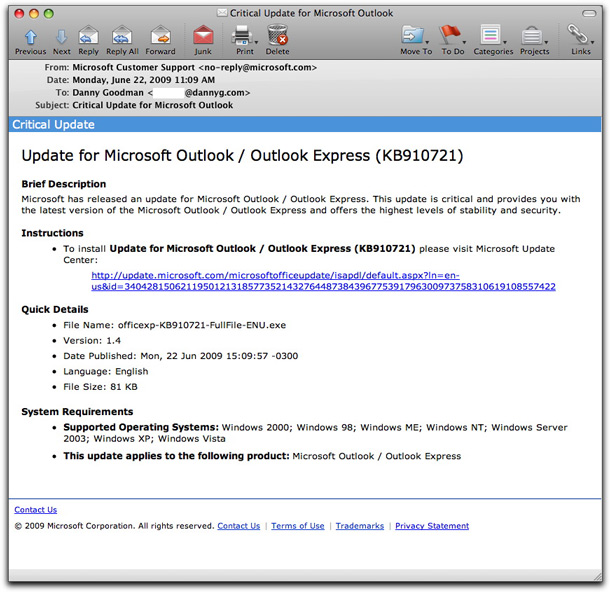
Bogus Microsoft Outlook Update Email
Here is an email claiming to come from Microsoft alerting Outlook and Outlook Express users to a supposed update:
This is a variation on the malware delivery email reported a few days ago by Sophos (and others), but this time the email doesn't carry an attachment, just a link. The link actually goes to a new site whose domain was registered waaay back earlier today. The destination page includes an iframe whose contents do the dirty work of pwning your PC.
Remember: Microsoft does not send out emails about critical updates. Use only the built-in Software Update mechanisms within Windows (and hope like hell your PC hasn't been previously taken over).
UPDATE 23 June 2009: The "Date Published" field of the message increments with the date on which the email message was sent. Also, the long number assigned to the "id" attribute in both the fake and real URLs change with each email.
UPDATE 23 June 2009 (#2): These emails have turned into a flood being sent from compromised PCs on most continents and using email addresses that included harvested spamtrap addresses — commonly recipients of medz and sex spam when the botnet recruitment efforts diminish.
Posted on June 22, 2009 at 11:41 AM
For the past couple of weeks I've seen the following types of messages come through:
Subject: Thank you! Your Order will be shipped within 24 hrs
Thank You!
Your Order Has been Processed and Will Leave our Warehouse in 24 Hrs!
Order Refrence ID: {%MIXED%}{%MIXED%}-{%MIXED%}{%MIXED%}{%MIXED%}{%MIXED%}{%MIXED%}{%MIXED%}
Please Visit http://[removed].com
---
Sincerely *Order/Processing Dept*
All those "{%MIXED%}" strings are placeholders for the botnet software to insert randomized numbers or letters to generate a so-called "Order Refrence [sic] ID". The stupid medz spammer hasn't figured out how to get the mail merge feature of his rented botnet to work.
Unfortunately that probably doesn't stop a lot of recipients from clicking the link in their haste to protest an order they didn't place (and isn't leaving any warehouse in any case). Sadly, and despite the snafu, enough newbie recipients will probably click the link anyway, and tick the hit counter of the spammer's web site. ROTFC[rying].
Posted on June 22, 2009 at 09:13 AMJune 21, 2009
419er Chutzpah
The height of criminal impudence is when a crook claims to be saving the impending victim from the very crime about to be committed. For example, malware distributor advertisements display false alerts about one's PC being infected so that the victim will install the real malware in the belief that they're cleaning their machines. And then we have advance-fee scammers (aka 419ers) who use words as their primary weapons, leaving plenty of opportunity for them to practice this type of audacity while twisting the minds of their email recipients.
Arriving today was a missive claiming to come from the United Nations. The message starts off with some impressive-looking images:
Then comes the message that essentially claims to offer the recipient $650,000 as compensation for having been scammed in any number of ways:
Attn: Sir/Madam,
Note! after series of meeting that lasted for three (3) Months with the secretary General of the UNITED NATION. You fall on the names submitted to receive a United Nation Compensation. This goes to all the people that have been scammed in any part of the world, the UNITED NATION have agreed to compensate them with the sum of US$650,000.00 (Six Hundred And Fifty Thousand United States Dollars) This includes every foreign contractors that may have not received their contract sum, and people that have had an unfinished transaction or international businesses that failed due to Government problems etc.Your name and email was in the list submitted by our Monitoring Team of Economic and Financial Crime Commission Observers (EFCCO) and this is why we are contacting you, this have been agreed upon and have been signed. You are advised to contact Mr. Sam Daws, as he is our appointed person for payment endorsement, contact him immediately for your International Bank Draft of USD$650,000.00 (Six Hundred And Fifty Thousand United States Dollars) This funds are pay-able in handy collection for security purpose, Therefore, you should send him your full Name and telephone number/your correct mailing address for dully processing of your claims.
Person to Contact: Mr. Sam Daws
Email: samdaws.[removed]@gawab.com
Phone No: +44[removed]
Country: United Kingdom.
Good luck and kind regards,Mrs. Inga-Britt Ahlenius.
[United Nations Seal image]
Auditor General of Kosovo (United Nation )
Making the world a better place
Although the forged From: address of the email says it's from unitednation.org (a parked domain, and not the official un.org), the gawab.com return address where victims are to begin their path toward financial ruin is a free hosting service in Saudi Arabia. Very run-of-the-mill scam bait tactics there.
419ers have invoked the United Nations frequently before. The U.N. is a good target because it has a feel-good vibe about it in recipients' minds (well, unless you're from North Korea I suppose), and the organization won't bother to pursue these dime store crooks for abusing a good name. But all that this 419er needs is for one sucker to get caught up in wiring money to cover various fees, documents, and taxes in order to free the (non-existent) $650K. A few grand will make the scam pay off and help fund the next round.
Posted on June 21, 2009 at 10:55 PMJune 17, 2009
Time to Slap a Wannabe Crook
My friends will tell you that by my very nature, I dislike violence. But when an emailing crook not only plans to rip off innocent victims and he wastes everybody's time (including his own) by being stupid, I just want to grab the guy by his necktie and give him a good slap across the face. It would be meant as a deterrent to not try this again.
What triggered my violent side today was yet another 419er with a lottery, or rather "award", winning announcement that stupidly exposes 400 recipient email addresses in the message (apparently a magic number for 419ers). There was also a glitch in his botnet that caused more than three-fourths of the list to appear in the body of the message.
The letter from "Mr. Stafan Smith" opens:
Dear esteemed recipient,
That's in the singular. What are my 399 co-recipients supposed to think? Does that mean that all 400 of us share the same "winning code"? (Sshh! It's 09PAD.) I'm not splitting the $2 million 400 ways. No way, dude!
How did I/we qualify for this award?
You have been selected due to the fact that you have sent more than 3 txts/email messages in 2months
Let me at 'im!
Posted on June 17, 2009 at 01:25 PMJune 14, 2009
Lame (and Phony) Microsoft Lottery
Advance-fee (aka 419) crooks never stop. Microsoft's name has been used in the past for lotteries, so it's not unexpected to see their brand so brazenly hijacked for this latest tall tale:
From: "Microsoft Corporation"<freewebprize@microsoft.com>
Subject: Microsoft EU Email Program..Your Email Won!
***********************************DO NOT DELETE THIS MESSAGE*****************MICROSOFT CORPORATION
EU INTERNATIONAL
EMAIL PROGRAM
P.O.BOX 7213
UTRECHT.
Tel: +31 [removed] 293 565
Fax: +31 [removed] 446 952
Microsoft Corporation wishes to congratulate you for being one of the lucky
winners in this season's email cash award program. With the introduction of
new types of games, with the ushering in of on-line technology and with the
permits issued under EU law to EU countries to compete for concessions to
run games on the internet, we are launching our first international
promotion.
This is an independent promotion and is unconnected to any publication.
No purchase necessary. Be informed that this lottery promotion was conducted
through the Internet worldwide random selection, we are running a program
where instead of bought tickets and numbers in the ballots we use email
addresses. All contestants were selected through a computer ballot system
drawn from email addresses taken from all over the world.
the participants and winners where picked randomly through a computer ballot
system and your email address have been selected as one of the lucky winners.Your email have been officially selected as a winner and authorised for
claim in the 2nd category winning prize of One Million Five Hundred
Thousand Euros.For payment of your winning prize outlined herein are the terms and
conditions for claims and onward transfer:1. You must be over the age of 18.
2. All winnings is Guaranteed and Insured.
3. Form below must be properly filled out.
4. Choose Mode of Payment (Bank wire Transfer / Bank Cheque)
5a.Winner is responsible for notarization fees and cost of transfer charges:
Due to the Insurance Bond Policy on your winning prize,
of which your winning prize must reflect exact winning prize on your nominated mode of payment.
(Bank Wire Transfer/ Bank Cheque) to avoid complications.6. The notarization of your winning certificate completes the
claim process, failure to do so will make you to forfeit the prize.7. Any leak of your winning information resulting in a double claim, will
nullify your winnings.8. You are obliged to have your name published as a winner and will be
invited to be present in the t.v.show after remittance.9. To be eligible for claim you must complete the claims process before the
expiry date stated in this winning notification you received.10. Filing a claim means acceptance of the full terms and conditions of
Micrsoft Corporation.If you agree to the terms and conditions for claim and onward transfer of your winning prize,
send your details and reference below to the Public Relations Officer below that you agree to the terms and conditions of
Microsoft Corporation and that you wish to claim your winning prize for onward transfer.
CONTACT:
MICROSOFT WEB
P.R.O
BOUWMAN WODERICK (MR).
Tel: +31 [removed] 293 565
Fax: +31 [removed] 446 952
Email: [removed]@WEB.NLSend the following to the Public Relations Manager above by email or fax:
Coupon Number: 378-059-132
Reference Number: WIN/83470/XEU
Full Name:
Date of Birth:
Occupation:
Address:
Country:
Telephone:
Email:
Winning Prize:
Proof of identity:Send your details by fax if you find it difficult sending an email.
Any leakage of this winning notification leading in a double claim will
makes you to forfeit your prize this is part of our security protocol,
thus we advise you to keep this winniKEEP THIS WINNING NOTIFICATION AWAY FROM PUBLIC NOTICE UNTIL AFTER TRANSFER.ng notification message confidential
away from public notice to prevent double claims and impersonation until after
remittance/payment to you.Note: Claim expiry date is 17-06-2009. After this date all winning prizes will be filed
as unclaimed.
Congratulations once more from all members of staff.
Management,Magaret Kexter.
(Co-Ordinator)
Microsoft Corporation.
NOTICE: This message, including all attachments transmitted with it, is for
the use of the addressee only.
It may contain proprietary, confidential and/or legally privileged
information. No confidentiality or privilege is waived or lost by any
mistransmission. If you are not the intended recipient, you must not,
directly or indirectly, use, disclose, distribute, print or copy any part of
this message. If you believe you have received this message in error, please
delete it and all copies of it from your system and notify the sender
immediately by reply e-mail.
© 2009 Microsoft Corporation. All rights reserved. Terms of use. Privacy Statement
Even if, in your greediest moment, you bought into the notion of winning money from the billions stashed away in Microsoft cash on hand, there is one telltale sign that this offer is bogus: The return email address is not to a Microsoft entity. Microsoft (who, incidentally, would know how to spell "Microsoft" consistently throughout an email message -- see No. 10 above) would never rely on Nederland Online (web.nl) for a return email address.
Notice, too, that these crooks are pre-lubricating the shafting they're going to inflict on anyone who falls for the bait:
5a.Winner is responsible for notarization fees and cost of transfer charges: Due to the Insurance Bond Policy on your winning prize, of which your winning prize must reflect exact winning prize on your nominated mode of payment. (Bank Wire Transfer/ Bank Cheque) to avoid complications.
That gets the recipient ready to fork over some up-front dough in anticipation of a big payday. It will start with a request for a few hundred dollars to be wired somewhere exotic, but eventually escalate to thousands or more. The only TV show any sucker will be on (see No. 8 above) is one of those investigative shows that lets repentant suckers tell their tales of woe at having been bilked out of their retirement savings.
Why don't these guys come up with something more believable...like Steve Ballmer personally handing your winnings to you as a bushel of cash?
Posted on June 14, 2009 at 10:22 PMJune 05, 2009
Work From Home! Go to Jail!
An unsolicited email message finds its way into your inbox offering the prospect of an easy job "processing payments" for an international company that needs an agent in "your area" (wherever you live). I've even seen some offers abusing brand names such as Federal Express in the mix. All you need is a computer (Duh, you have email!) and a bank account.
If you bite for this trick, you'll soon be setup as a money mule, laundering funds lifted from stolen bank and investment accounts. The accounts were hijacked through your employer's surreptitious installation of Trojan software that grabs login keystrokes (usernames and passwords) to financial institutions. Of course, that happens in an entirely other "department," so you're not aware of that part of the business.
The "job" actually pays well in that you keep a sizable share of the funds deposited in your account, while you wire the rest to your "boss" in another country. Little work. Big rewards.
Oh, did I mention the risk? Ah, you see this "job" is totally illegal in the United States. Just having the stolen money deposited into your account is a crime. Passing it onward only adds to the offenses.
According to The Register, New Hampshire resident Alexey Mineev got caught up in one of these schemes and pleaded guilty to money laundering. He's having to cough up nearly $112,000 that the Feds observed him skimming over 16 months, and he may also spend time at the Graybar Hotel.
And you thought your job sucked!
Posted on June 05, 2009 at 04:11 PM