| Home | The Book | Training | Events | Tools | Stats |
July 21, 2006
From the FBI...NOT!
Here is a malware propagation message I received that is bound to catch plenty of unsuspecting folks off-guard:
Dear Sir/Madam,
We have logged your IP-address on more than 30 illegal Websites.
Important:
Please answer our questions!
The list of questions are attached.
Yours faithfully,
Steven Allison
*** Federal Bureau of Investigation -FBI-
*** 935 Pennsylvania Avenue, NW, Room 3220
*** Washington, DC 20535
*** phone: (202) 283-2717
There is a 3.2 kilobyte file attached called Questions_List.zip. Viral analysis shows it to be a Trojan loader—a tiny program that reaches out to a specific place on the Internet and downloads more nasty stuff that takes over your computer.
Probably 80% of Internet users don't know what an IP address is, and 99% of Internet users wouldn't know that your IP address (which is usually logged when you visit a web site) does not reveal your email address. Technically, the content of this message is bogus, but it sure sounds possible to the non-geek.
By the way, as I'm a proponent of checking the least forgeable part of an email message's header to see where the message really originated from, I can say with high confidence that the United States FBI does not send mail through a German email server. That's where the one I received came from (probably another compromised PC).
Posted on July 21, 2006 at 11:57 AMJuly 18, 2006
A 419er's Direct Approach
Most of the "help me transfer umpteen million dollars out of Africa" email scam messages come with colorful stories of deposed diplomats, intestate oil executive deaths, or fear of dictatorial regimes coming after the families and secret assets of murdered politicos. The English is usually, at best, broken, and perhaps the combination of a long, sad story in a second-grade English composition pulls at the heartstrings of recipients.
Well, no, those characteristics have nothing to do with those who fall for it. The recipients are simply greedy and lazy, hoping to cash in on someone else's misfortune, even if it means committing a few white-collar crimes along the way.
One 419er obviously understands the bottom line of the appeal, and doesn't bother concocting a tearful tale of woe. He comes right to the point:
Attention Sir
I am the Chairman of the Contract Award Committee(CCAC), Ministry of Mines and Energy,Namibia, We need a trust-worthy partner to assist us in the transfer of Twenty Two Million United State Dollars(US$22M). And subsequent investment in properties in your country.
You will be required to:
(1) Assist in the transfer of the said sum to your country for a viable business
(2) Assist us in purchase of properties.
If you decide to render your service to us in this regard, 22.5% of the total sum will be offered to you. Please, kindly get back to me if you willing to assist.
Yours Faithfully
John M. Titus
The supposed payout for this one—nearly $5 million—may be good enough for any greedy Gus to make that one big, final score. Just reply to the free netscape.net email address to get started.
Of course the $5 mill is also enough of a cushion to let the crook con any taker into forking over many thousands of dollars up front for the inevitable fees, taxes, bribes, bank transfer mistakes, blah, blah, blah. The only pot at the end of that rainbow is a flusing toilet.
Posted on July 18, 2006 at 04:39 PMJuly 12, 2006
When Does Spam Become Harassment?
A rather insistent mortgage lead spammer keeps the barrage coming. Somewhere along the line, the email address list used by this jerk has been matched with my street address. This allows his spew machine to make the message sound more personal by including my street address in the message.
Most recently, the address has been right in the Subject: line, along with typically deceptive words aimed at getting my attention and luring me to open the message. Now, I know how all of this works, and it's highly automated, but I wonder if someone receiving the same flood of email seemingly targeting the physical residence might become frightened, especially when the Subject: lines sound threatening, at times—as if someone is selling your house right out from under you. Even though I know how this works, it's still creepy getting a message from a spammer who knows more about me than I like.
I pulled together a recent list that used this street address tactic, and present the results below (with my street address redacted, just as I do with the copies I forward to the FTC just in case they should become evidence in future litigation against the perp):
This has gotten waaaay out of hand. As of today, this guy started using a new domain registration name/address/phone combination. This time, it's another Florida city, but the street address doesn't exist, and the phone number is for a Pennsylvania area code.
Unfortunately for me (and others who received this threatening material), it will take someone with resources to trace the ass behind this campaign. It will take subpoenas and all that legal stuff to reach the true source. Oooh, I hope MSN customers have received a lot of these, because Microsoft isn't afraid to go after this type of CAN-SPAM scofflaw (Yay, Aaron Kornblum!).
Posted on July 12, 2006 at 07:43 PMJuly 08, 2006
Phishers Will Try Anything, Part Deux
Same day, different message trick:
Hello Member,
Your monthly eBay Invoice is now available to view online.
Invoice Date: July 09, 2006
Amount Due: $14.67
You can review your current invoice details and account status at any time by clicking on View Invoice <http://REMOVED_FOR_YOUR_SAFETY.net/images/unused/ws/eBayISAPI.dll/SingIneBay.html>
For future reference, you can access your invoice by following these steps:
1. Go to the eBay Home page.
2. Click My eBay at the top of the page, and sign in with your eBay User ID and password.
3. Click the "Seller Account" link (below My Account in the left navigation menu).
4. Click the "Invoice" link.
Regards,
eBay International AG
The link leads to a lookalike eBay login page hosted in Australia. Fortunately, this clown didn't know enough HTML to disguise the link, so let's hope it won't fool many recipients before the hosting service takes it down.
Posted on July 08, 2006 at 10:01 PM
The PSYOPS (Psychological Operations) Department at Phishing Crooks Central is working overtime to come up with what appear to be credible missives from eBay. Their goal is to get the unsuspecting eBay member to click on a link that leads to a bogus eBay login page. Once they capture your username and password, your account will likely be hijacked and used for fraudulent purposes. The password will be changed so you can't even get in there to fix it. If you've built up, say, double-digit reputation points, they'll be used by the scammer to flog non-existent goods.
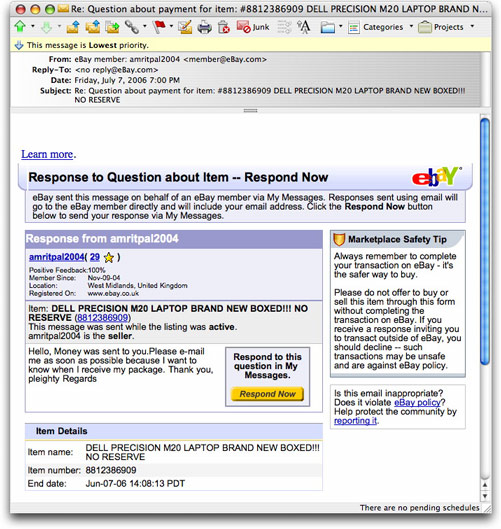
Here is a scam message I saw today. It purports to be a response to a query that I supposedly sent to request payment for a computer. The message has many (but not all) the trappings of being from eBay's message system, which eBay rightfully encourages its members to use to communicate with other members.
Experienced eBayers would, I hope, recognize this as being suspect for one important reason: the message doesn't address the recipient by eBay ID name. That should be alarm bell Number 1. Of course the real alarm bells, as I've stated many times, are in the source code of the message. For instance, when you'd expect the message to originate from an eBay server, it comes instead from a Tampa, Florida Verizon DSL customer's hijacked computer.
But even if you're not willing to take the ten minutes to learn how to perform that kind of fraud detection, there are plenty of other harmless things a recipient could do to investigate this matter.
Start with the auction number. NOT the link in the message, but the raw number, which is easy to search in the real eBay site by placing it in any Search box. Unlike some earlier scams, this one leads to a real auction. The "item details" at the bottom of the message are all accurate, except for the end date. The real auction ended on May 22nd, not June 7th.
The phisher must also be very confused (or doesn't have a complete grasp of English). The message says, "This message was sent while the listing was active. amritpal2004 is the seller. Which leads to a kinda obvious question: Why would the seller send me money and expect a package from me?
Phisher's grade in Logic 101: F
(Looking deeper into that auction is also enlightening. The seller, jalaya69, is listed as "Not a registered user." The membership started on November 9, 2004, and for a year-and-a-half, this member was only a buyer of other peoples' stuff, and had built up a 100% positive feedback rating. Suddenly, in May of this year, the member became a seller of computer and cell phone stuff. In June, negative feedback started coming in. I believe that this account had been hijacked by a phisher and taken over by a crook [albeit a small-time one]. eBay eventually shut down the account, but the original member, if he or she is still involved with eBay, had to start over.)
eBay also lets you look up a member by name (in the Advanced Search page). Entering the sender's name from the email message, you'd find that there is no member by that ID. There are some close ones, but not this specific one. And, talk about coincidence (not!), the phishing message claims that amritpal2004 has been a member since November 9, 2004—the same day that the auction's seller of record joined eBay. Even more evidence in my eyes that the actual auction seller's account had been hijacked.
I receive so many phishing messages claiming to be from PayPal and eBay (I belong to both) that I'm ultra-suspicious of any message with those dot-com names in the From address. I have separate and unique email addresses that are associated with my accounts, and the phishing messages are always addressed to my long-time, now-completely-hosed, standard email address. That also helps me weed out the phony from the real. But even when a real one comes, I take the time to validate it myself. And then I never, never, never click on any link or URL in one of those messages. Instead I manually enter the site (or use a bookmark from a previous manual visit) and check my account.
It's all a horrible pain in the ass, but crooks have largely destroyed email as a viable communications medium between financial sites and their customers.
Posted on July 08, 2006 at 10:30 AMJuly 06, 2006
On the Internet, Nobody Knows You're a Liar
One of my all-time favorite New Yorker cartoons shows two dogs, one sitting in a chair in front of a personal computer, the other down on the floor. The dog in front of the PC says to the other, "On the Internet, nobody knows you're a dog." You can even buy a reprint (no kickback to me).
Considering that the cartoon first appeared in July, 1993, it was more than prescient about what has happened on the Web. Our computer pup may have been thinking more about chat rooms (or, rather, only bulletin board systems—BBSes) at the time, because the World Wide Web was barely up and running at that point. Today, as we see constantly with very credible phishing lookalike sites and such, a Web site's bullshit factor can be anywhere from 0 to 100%.
I was scanning a considerable backlog of spam suspects from my server today and saw a lot more of the mortgage spam about which I complain often here (three times last month alone: [1], [2], [3]). I was checking up on the domain records of a bunch of spamvertised domains from the same gang. They had all been registered to a bogus Chicago address for quite awhile, but they had changed recently to a bogus Florida address within the past few weeks. I'm not sure what it was going to tell me, but I wanted to know when the switch occurred. The switch also included going to a new registrar (directNIC), with whom I've filed numerous disputes for false domain registration records (and, in usual fashion, have received no response whatsoever).
The disputes center on the registration records for over a dozen domains that are registered to an individual name claiming to be at an address in Clearwater, Florida. Problems with the records include the fact that: the ZIP code is for Atlanta, Georgia; the telephone area code is invalid anywhere in North America; the street address is not valid for Clearwater or Atlanta. As for the yahoo.com mailing address, well, let's just say I'm dubious. Also, the "organization" name is listed as "Roflon," whose first four letters are everyone's shortcut for "rolling on floor, laughing."
By accident I accessed the Web site from the earliest spam message pointing to one of these Roflon domains. I wanted to kick myself when I watched the browser's Address field flip and flop around to eventually include code that signified an affiliate ID not part of the URL I used. It's possible that the spammer got a fraction of a penny chit for that visit, and that really pisses me off.
So, anyway, there I was at this slick-looking mortgage lead site that promises "Hassle-Free Quotes." The site is not SSL encrypted, nor is the destination URL of the form on the page. But at the bottom of the page is this notice:
For your protection all information submitted through our secure website is confidential and will only be provided to the lenders that we work with.
Additionally, in a column of logos running down the left side of the page is one that says "Protected by VeriSign," a company that is a Certificate Authority for SSL Web sites. But there was nothing on this page (which asked for information about mortgage types and amounts) that was secure.
Also in that column of logos was one for Trust*e, a service that reviews Web site privacy policies and allows those that pass muster to post the logo. Except this site offered no link to a privacy policy. Ooh, not even close, and certainly no cigar.
Finally, the logo that really made my blood boil was the logo that says, "We are fully compliant with the CAN-SPAM Act of 2003." So I guess the deceptive Subject: line and message, failure to identify the sender, forging headers, not offering an opt-out link, and sending through a Trojaned PC of a Comcast cable customer in New Jersey don't count.
Although I was already feeling creepily filthy just looking at that page, I did a further check of the source code. The server that sent the page had embedded the affiliate ID and my IP address into hidden fields of the form that would have been submitted. I'm not worried about the IP address because I access the Internet through a dynamic system that changes fairly frequently (and unexpectedly with outages...grrr). But I wasn't going to even put bogus data into the form and visit the next page out of desire to stop my "support" of the affiliate with my single, accidental visit.
If I sit back and examine the page with the eyes of a typical Web surfer—perhaps one interested in refinancing a mortgage—I'd have to say the site looks legit. I mean, look at all those security, privacy, and anti-spam logos appearing so prominently. And the art and layout look professional. It must be a great outfit with which to do business.
And, thus, the title of this article.
Posted on July 06, 2006 at 03:43 PMJuly 02, 2006
PayPal Phisher Using the Bogus Charge (Again)
It's a tactic I've seen often. Only the names change to protect the guilty.
Today's PayPal phishing message claims to be a confirmation of a payment made from your account in the amount of $474.99 for a Nokia Cell Phone to LWPELECTRONICS. The shipping address is to somewhere in Maine, an address that seems familiar to me from previous similar pitches for Sony products.
The claim ends with this kind of thing:
If you haven't authorized this charge, click the link below to cancel the payment and get a full refund.
The link takes you not to PayPal, but to a hijacked server in South Korea that displays a PayPal login lookalike page. No, it's not hosted at bora.net, but the owners haven't done anything about it for the last 18 hours. Sadly, par for the course.
If you ever get one of these things and still wonder if there is a charge on your PayPal account, log into your account the normal way—not by clicking the link in the email—and check your account history. You'll find no such activity in your account to dispute.
Posted on July 02, 2006 at 08:05 PMJuly 01, 2006
How bora.net Solved Its Internet Abuse Problems
It's an all-too-common situation. A spam or phishing reporter tries to follow an ISP's procedures to submit a report about suspected fraudulent activity, only to have it be rebuffed. In this case, I had an IP address of a South Korean server that had been hijacked by phishers. There was no contact information or domain name on the site's home page, so I started with the phishing link, which was an IP address.
I look up the IP address and find that it belongs to bora.net, self-described as the following:
descr: DACOM Corp.
descr: Facility-based Telecommunication Service Provider
descr: providing Internet leased-ine, on-line service, BLL etc.
The record also invites viewers to submit reports to abuse and security email addresses. Which I gladly do.
A moment later, I receive a bounce message with the following advisory:
Recipient's maiilbox is full, message returned to sender, (#5.2.2) [7mallot:(209715200), usage:(220909568)
In other words, their approach to abuse reporting is to cover their ears, close their eyes, and shout "la la la la la la." That way they never have a problem. I've sent hijacked web site reports to their security address before. Although those messages didn't bounce, the sites stayed up for weeks.
I did find the web site of the parent company, Dacom, and they have an English version of the site. Unfortunately for me, it's all about selling services and not servicing. The formal contact email address is to the Webmaster of the site. Something tells me my report won't get very far.
South Korean ISPs have a reputation of not being responsive to Internet problems that ooze out worldwide. If you check a Korean IP address against DNS blocklists, you'll commonly find snide messages accompanying the listing, such as "we do not accept mail from korea" and "korea does not seem to care about spam." Although I understand that some ISPs have taken steps to do things like curbing spam spewed by zombie PCs, problems obviously persist. And some ISPs really don't seem to care.
Posted on July 01, 2006 at 10:48 AM