| Home | The Book | Training | Events | Tools | Stats |
December 27, 2011
Post-Christmas Malware Lure
This one has all the hallmarks of a so-called script kiddie. It's school holiday time for lots of teenagers around the world, so it's not unusual to see a rise in what these kids think is clever fooling around to earn some pocket money. Ultimately, the email link (if it had been executed properly) leads the unsuspecting recipient to the old main.php program, which serves up a boatload of obfuscated JavaScript malware loading code.
To get the recipient all riled up, the crook employs a common tactic:
Subject: Re:IRS NOTIFICATION:-Complaint against your business af8d0a35bfd97efb
Nothing like invoking the tax folks to get the adrenalin flowing.
The message body goes horribly wrong in the way it had been deployed, but here's what shows up in my email client:
308389540413852-78-0055
<!--We regret_to_inform_you, that link--> goo.gl/[removed]
The HTML commented part looks like the start of boilerplate code, complete with a mail merge-like placeholder (the underscored bit). From the looks of it, the kid screwed up the composition of the body and didn't test before deploying (Kids!). He (or she) did insert an active URL, using a Google URL shortener, but not as a clickable link. To save you the trouble of copying the URL and pasting it into a browser, the journey continues through a freshly-minted domain containing further redirection until your browser lands at an India-based server hosting the main.php program. That's where the JavaScript looks for all the usual Windows security holes.
At the same time, the malware lure campaign using a phony contract as bait continues. Today's installment makes it sound like the contract process has gone further until the latest snafu:
Subject: The variant of the contract you've offered has been delcined.
After our legal department studied this contract carefully, they've noticed the following mismatches with our previous arrangements. We've composed a preliminary variant of the new contract, please study it and make sure that all the issues are matching your interests
NEW_Contract.doc 20kb
With Respect
Jorge Prescott
MD5 check sum: 8c46c46c4138ce9a52180726c413338c
As before, the link is not to an attached document but to a Russian server hosting the main.php code.
Ya de yadda.
Posted on December 27, 2011 at 12:13 PMDecember 21, 2011
Fake BBB Malware Lure
Today's lunchtime inbox morsel is a message aimed at the industrious small business worker/owner who tries to keep the company's customer reputation in first-class condition. The message claims to represent the Better Business Bureau, who has supposedly received a complaint from a customer.
Subject: Your customers concern
Better Business Bureau®
Start With Trust®RE: Case # 58871023
2011/12/21Dear Sirs,
The Better Business Bureau has got the above-referenced complaint from one of your customers regarding their dealings with you.
The details of the consumer's concern are explained in attached file.
Please give attention to this case and notify us of your opinion.
We encourage you to open the ATTACHED REPORT to answer this complaint.We look forward to your urgent reply.
Sincerely,
Shawna Dennis
Dispute Counselor
Better Business Bureau
Privacy Policy | Terms of Use | Trademarks | Find a BBB | BBB Directory
© 2011 Council of Better Business Bureaus
In addition to the many grammatical errors in the message, the forged headers of this message are a mess. The From: field shows an address from a legitimate web site domain — not the BBB; the To: field is addressed to someone at cya.ca.gov (the California Youth Authority). Now I'd wager that some of the CYA's "customers" complain, but not through the BBB.
Although the action item of the message indicates that the complaint is in an attached file, instead there is a link to a hijacked web site. The offending page had been taken down by the site's owner (Way to go!), so I don't know if the page contained the main.php iframe or script download technique. Poker professionals will tell you that if you are bluffing, the story you're representing has to be solid so your opponent(s) can believe your bull. This one fails miserably.
I truly don't care where the links lead. I'd rather recipients be aware that this message — or any message that attempts to get the recipient all riled up and click-happy — is phony and potentially dangerous if they click the link.
Posted on December 21, 2011 at 04:05 PMDecember 14, 2011
main.php Vector Change
Well, it has been a "good" run for the main.php guys. Perhaps they got as tired of their drive-by technique as I did receiving their messages. In today's latest, the messages have a similar ring to them, primarily focused on some alleged FDIC transaction nonsense. Here are a few examples of the messages:
Subject: Suspension of your transactions
Dear customer,
In order to diminish the number of wire fraud cases, we have introduced a new security system. In this connection all the ACH and WIRE transactions of our customers will be suspended until your security version meets the new requirements.. In order to reinstate your account abilities, you are required to install a special security software. You may use the link below and follow the instructions to proceed with the installation.
http://fdic.gov/updates/49378441
We apologize for causing you troubles by this measure.
Please do not hesitate to contact us if you experience any problems.Yours truly,
Federal Deposit Insurance Corporation
Security Department======================================
Subject: For the urgent attention of Accounting Dpt.!
Dear Sirs,
In connection with the introduction of a new security system for the purpose of preventing new cases of wire fraud, all the ACH and WIRE transactions on your account have been blocked until your security version meets the new requirements.. In order to re-establish the full functioning of your account, you need to install a special security software. Please open the link below to read the instructions and download all the necessary files.
http://fdicgov/updates/96042318
We apologize for any troubles caused to you by this measure.
Please do not hesitate to contact us if you have any questions.Sincerely yours,
Federal Deposit Insurance Corporation
Security Department======================================
Subject: Urgent notice from FDIC
Dear Sirs,Due to our adoption of a new security system, for the purpose of preventing new cases of fraud and scams, all your account ACH and WIRE transactions will be suspended until you update your security version in compliance with our new requirements.. In order to restore your ability to make transactions, you are required to install a special security software. Please open the link below to download and install the latest security version.
http://fdic.gov/updates/28009746
We apologize for causing you inconveniences by this measure.
Please do not hesitate to contact us if you have any questions.Yours truly,
Federal Deposit Insurance Corporation
Security Department
The links beneath the visible fdic.gov links go to hijacked web sites as before. But instead of loading the main.php URL into an iframe, these hijacked site pages load not one, not two, but three copies of a script, each from a different hijacked site — a redundancy that plans against possible shutdowns/cleanups of one or more sites. The scripts are loaded via simple <script> tags, and all three sources end in jqueri.js (not related to JQuery). The scripts consist of obfuscated JavaScript which decodes itself to execute a laundry list of JavaScript-controlled exploits on malware-susceptible PCs.
As an extra bonus, when the decoded script finishes, its last task is to redirect your browser to yet another site that has been known to load malware. Your browser — and perhaps your PC — will have been beaten to a pulp before this sequence finishes.
Again, the actual exploits being abused in this campaign aren't important to everyday users. But the social engineering techniques in the opening email salvos definitely are. Resisting to click on ominous links is hard. But resist you must!
Posted on December 14, 2011 at 12:25 PMDecember 13, 2011
main.php Malware Lures Continue
In the apparently never-ending saga of the main.php malware lures, I saw two today, one of which was a variant of the Adobe CS4 license trick.
Here they are:
From: sales1@[my own domain].com
Subject: Re: Fwd: Order K90309811
Hello,
You can download your Windows Vista License here -
Microsoft Corporation
Like the earlier Adobe message, this one attempts to lure with a previous generation product license. Since the crooks aren't really giving anything away, I'm still puzzled why they flaunt a license for an outmoded version.
Subject: Im shocked!
Have you seen how much money has Cameron spent on his new movie?
What a graphics, check out the trailer!
Yes, both lines are underlined, but only the second one is a clickable link.
In the case of both messages, the actual links take victims to hijacked legitimate web sites, where the page contains an iframe that loads (from a URL that ends in main.php) an obfuscated JavaScript page from a Russian web site. Unlike antivirus sites that delve into the particular exploits being used by the malware attacks, I couldn't care less. My concern is teaching recipients of this junk to think twice — if not thrice — about clicking on links from unsolicited email.
Posted on December 13, 2011 at 09:47 AMDecember 09, 2011
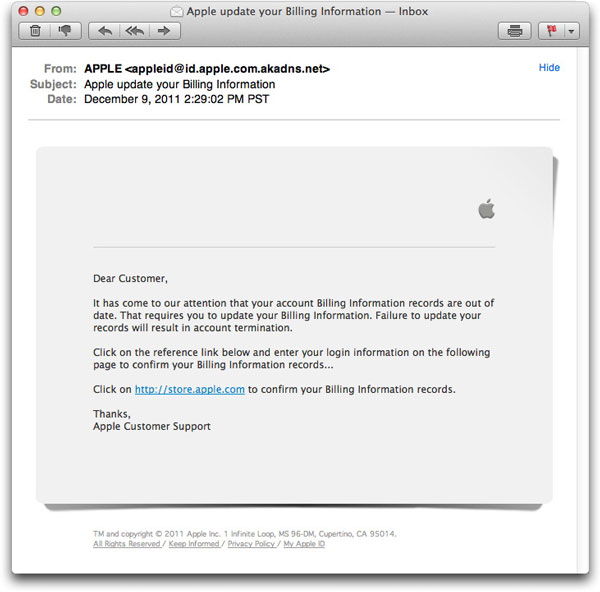
Phony AppleID Notice
Although the following item has been flowing around spamdom for awhile, I thought I'd show it just to demonstrate the lengths phishing crooks will go to trick recipients into giving up their login credentials and identity info.
This one claims to help you overcome a billing snafu at the Apple Store:
If you dare follow the link—the real link is to a site whose domain was registered yesterday—you'll be asked for your AppleID and password. After that you'll find a form requesting additional identity info.
Compromised Apple Store login credentials can really do damage if you don't catch it in time. Fixing it can be an even bigger headache.
Posted on December 09, 2011 at 08:13 PMDecember 08, 2011
More main.php Hijinks [Updated]
Today's episode of As the main.php Malware World Turns features another trick designed to fool recipients into clicking a dangerous link that eventually leads to the Russian-based main.php malware loading page. These tricks have been reported here more often than a Kardashian appears on TMZ.
The subject matter of the latest is some vague contract that's supposedly of interest to you. Here's a sample:
Subject: Your new contract
As we arranged on our last meeting in the office we've got the contract ready, plase study it carefully and let us know whether you accept all the issues.
We've attached the copy of the contract below
Contract.doc 122kb
Best wishes
Laverne Bennett
MD5 check sum: a5e61bd3afa5495e1954b20849faf7d8
There is no attachment. Instead the clickable link goes to a hijacked legitimate web site, where the page loads the Russian-based main.php page into an iframe element. The checksum at the end is completely bogus — just like the so-called "fingerprint" of other messages in this campaign.
A second variation also arrived today:
Subject: Re: Fwd: Changelog New
Good day,
changelog update - ChangelogVICK GALE
Fingerprint: 95e1b203-af72084b
Just vague enough to make it look harmless. But it's not. By the way, if this looks familiar, take a look at this Spam Wars Dispatch from June, 2010. Coincidence? No. Same asshole switching between malware loader attachments and links.
Sadly, I believe the creator of the more recent messages leading to main.php has a good handle on what tricks unsuspecting recipients into clicking links. And that makes me mad.
Update (9Dec2011): I saw another version of the contract malarkey:
Subject: The variant of the contract you've offered has been delcined.[sic]
After our legal department studied this contract carefully, they've noticed the following mismatches with our previous arrangements. We've composed a preliminary variant of the new contract, please study it and make sure that all the issues are matching your interests
Contract.doc 48kb
With best wishes
Beatrice Mcneil
Secure Checksum: 0417d5b304641
Same trick, different wording to get past your best brain defenses.
Posted on December 08, 2011 at 09:12 AMDecember 07, 2011
Pizza With Extra Malware
Reminiscent of the teenage prank of ordering a pizza for delivery to an unsuspecting friend (or enemy), this week's malware lure tries the same trick, but without the actual delivery.
The email claims to be an order confirmation for one giant pizza party. The From: field is populated with randomized plug-in names, such as "CALLISTO's Pizzeria" or "Pizza by Giacinto". The makeup of pizzas and other goodies varies from message to message, but here's an example:
You’ve just ordered pizza from our sitePizza Supreme with extras:
- Italian Sausage
- Italian Sausage
- Green Peppers
- Green Peppers
- No Cheese
- No Sauce
Pizza Italian Trio with extras:
- Italian Sausage
- Green Peppers
- Extra Cheese
- Extra Sauce
Pizza Hawaiian Luau with extras:
- Beef
- Italian Sausage
- Bacon Pieces
- Onions
- Green Peppers
- Extra Cheese
- No Sauce
Pizza Spicy Sicilian with extras:
- Ham
- Green Peppers
- Jalapenos
- Extra Cheese
- No Sauce
Pizza Meat Lover's with extras:
- Beef
- Italian Sausage
- Pepperoni
- Diced Tomatoes
- No Cheese
- Extra Sauce
Drinks
- Budweiser x 5
- Coca-Cola x 2
- Gold Peak Tea x 2
- Cherry Coke x 3
- Mirinda x 6
- Red wine x 2
- Carling x 2
Total Due: 179.67$If you haven’t made the order and it’s a fraud case, please follow the link and cancel the order.
CANCEL ORDER NOW!If you don’t do that shortly, the order will be confirmed and delivered to you.
With Best Wishes
CALLISTO`s Pizzeria
Fingerprint: 7d5b8304-172d5b83
Not all of the messages have the "Fingerprint" nonsense at the end, but many other messages in this same campaign do.
Since no one wants to pay for over a hundred bucks of pizza delivered to his/her door, the adrenalin kicks in and the recipient clicks the Cancel link in panic. Rut Row! It's our old friend that takes you to a hijacked web site where an iframe loads the ol' main.php malware loading page [yawn].
And that, kids, is how botnets grow.
Posted on December 07, 2011 at 09:02 AM