« Dear PayPal Costmuer | Main | You Did NOT Win a FREE $1000 Apple iPad 2! »
| Home | The Book | Training | Events | Tools | Stats |
October 14, 2011
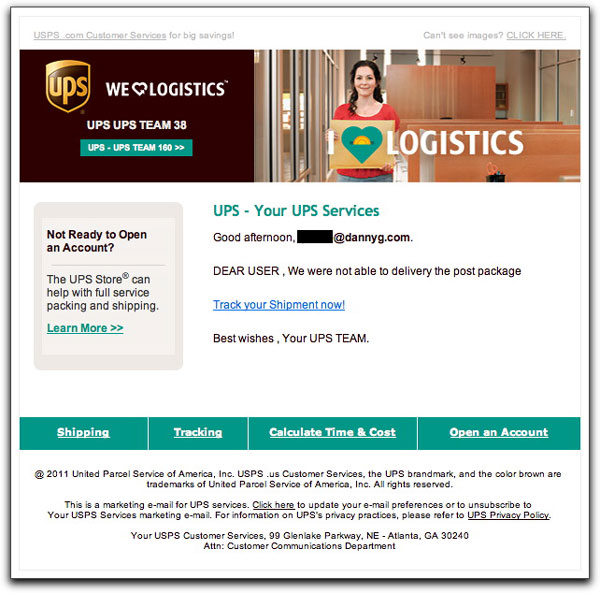
Confused Malware LureI suppose some folks confuse the United States Postal Service (USPS) with United Parcel Service (UPS), at least by name. The two organizations have created very different visual presentations for their logos and other material. The USPS wraps itself in the good ol' red/white/blue color scheme, while UPS is the Brown company. The two companies' marketing messages are very distinct.
A presumably non-US malware distributor hasn't yet grokked the distinctions. Today he sent a message:
Subject:United Postal Service Tracking Nr. H4222259476
WTF is the United Postal Service?
Now look at how a phony email message body uses lots of UPS images, while some of the fine print refers to the USPS:
There are so many other inconsistencies in this email (not to mention the major grammar booboo when they couldn't "delivery" the package) that it's really quite a mess. And having the From: address be an aol.com account doesn't help their believability case.
I was naturally curious about the link. Was it going to be to a medz site or a malware distribution point? Lo and behold, it goes to yet another of the main.php destinations I've been seeing. Although the domain was freshly minted a couple of days ago, it had not yet been shut down like the others (c'mon, registrar GoDaddy!). It did, however, give me a chance to find out what the main.php destinations are trying to serve up.
The source for the page returned by the main.php program consists of just one script tag with obfuscated JavaScript. When decoded (which, to the regular user would happen upon landing on the page), the script checks to see which potential vulnerabilities are available in the user's browser. Although some of the vulnerabilities are Old School ones, the script does perform a check for the fairly recent Chrome browser. Presumably, the attempts to load a variety of objects into the page are to alert the Bad Guy about which exploits will likely succeed with this user's PC.
I wouldn't want to go near that page intentionally with a browser, even if I had antivirus software installed.
Perhaps these guys think they're so smart with their double-obfuscated JavaScript. But with the simple stuff in the email presentation, they're dumb, dumb, dumb.
Posted on October 14, 2011 at 11:33 AM