| Home | The Book | Training | Events | Tools | Stats |
November 08, 2017
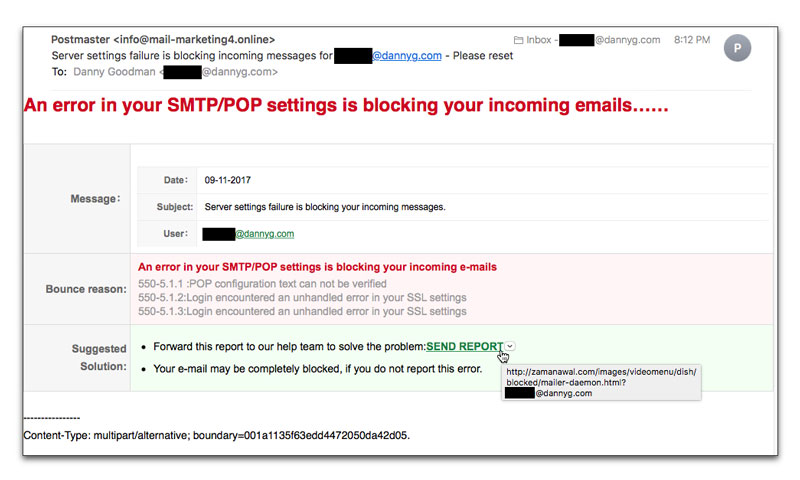
Fake Email Server Settings WarningAside from a little formatting ugliness, the following email is an unfortunately decent attempt to phish for your email password (and, then, conceivably, to your account on the server and further server intrusions from there).
The Subject: line is pretty threatening:
Server settings failure is blocking incoming messages for [redacted]@dannyg.com - Please reset
To many typical computer users, the "Bounce reason" data would appear as gobbledygook, but to someone who also manages the personal or business email server (perhaps at your domain's ISP), it's very plausible gobbledygook. But even if you don't know what it means, the message goes on to provide a convenient link to follow to send a report to the mail team so they can fix the problem.
And that's where you get into big trouble.
If you follow my forever guideline to rollover any link before clicking it (something that would have saved John Podesta from a dumpster full of trouble), you'll see the destination URL is something you probably don't recognize. The URL includes your email address (the one used to get this message to you in the first place), so that if you follow the link, you reach a similar-looking page in your web browser that pre-fills a field with your email address. There's no magic to this feat: Any 12-year old with a little bit of JavaScript experience could do it. But the other, blank, field requests your email password. Fill that in and submit it, and you're toast.
BTW, there is another telltale sign to this American that the message comes from someplace other than my American-based ISPs: The body specifies a date in the dd-mm-yyyy format, rather than the expected mm-dd-yyyy format. The date was filled in by the crooked email bot sending the email from somewhere in the Eastern Hemisphere. I know this because my email server processed the message in the U.S. late in the evening of November 8.
Be careful out there.
Posted on November 08, 2017 at 09:36 PM