« Do People Believe 419ers? You Bet! | Main | Riding the Coattails of Credibility »
| Home | The Book | Training | Events | Tools | Stats |
September 25, 2008
Malware Lure Spoofing CNN Web SiteThe news flash malware lure is on the march once again. This time, it's World War III. Here's the message:
Subject: The beginning of the Third World War.Important! The beginning of the Third World War: The Russians used nuclear weapon against Georgia. According to Pentagon, the bomb of 17 megatons in TNT equivalent (which equals to 27 bombs that were used in Hiroshima) was launched at Tbilisi, the capital of Georgia, from the Russian submarine in the Black Sea. According to tentative data, Tbilisi and its suburbs in the radius of 20 km have been leveled to the ground. George Bush, speaking in the name of the whole America, made an official statement, claiming the readiness of the USA and all the NATO members for the retribution operation against Russia and the use of nuclear weapon. Click the link below to view George Bushs address: http://cnnworld.org/index.php?video_id=75198
I normally block the URLs when relating these types of messages, but in this case, the domain name is an important part of the story.
In many past posts about apocalyptic malware lure messages, I recommend visiting legitimate news sites to confirm that the message is a hoax—by the lack of any mention of the end of the world. The site I typically turn to first is cnn.com, mostly because it's easy to type.
At first glance, the domain name in the message might look believable to many. It's short and sweet.
It was also registered yesterday.
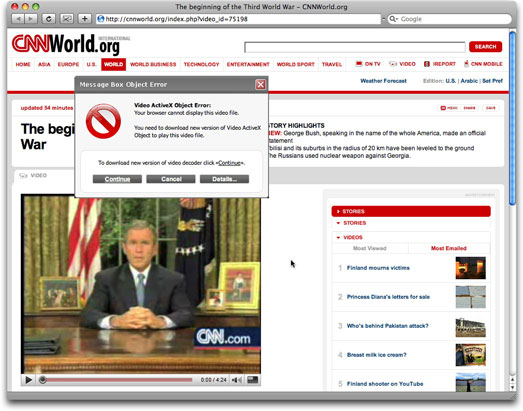
If you were to visit the URL in a web browser (DON'T DO IT!), you'd see a page that, again at first glance, has a believable look and feel of the CNN International page:
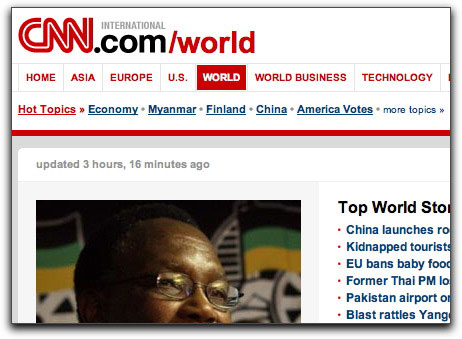
This is what the upper left corner of the real CNN International World page looks like:
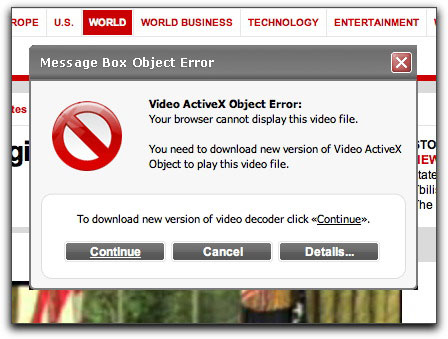
Now, onto the "dialog box" that talks about an ActiveX problem. Here it is in detail:
The alert is a Dynamic HTML absolute-positioned element made to simulate a dialog box window (it's even draggable). If you click the Details button, an alert dialog tells you to download the codec. If you click the Cancel button, you are placed into an infinite loop that forces you to agree to download the codec unless you kill the browser.
Of course, the download is no codec. It's a malware loader named codecpack.v.1.1.18.exe. Unfortunately, at this hour, VirusTotal shows a measly 17% (6/36) detection by antivirus products.
And the botnets grow....
UPDATE (2:54PM PDT 25Sep2008). The site is hosted in Iran, as are the domain's DNS servers. Domain name registrar is eNom.
Posted on September 25, 2008 at 12:09 PM