« 419er Uses Google Docs To Spread Scam [Updated] | Main | iPhone Rip Off (Sans iPhone) »
| Home | The Book | Training | Events | Tools | Stats |
October 21, 2009
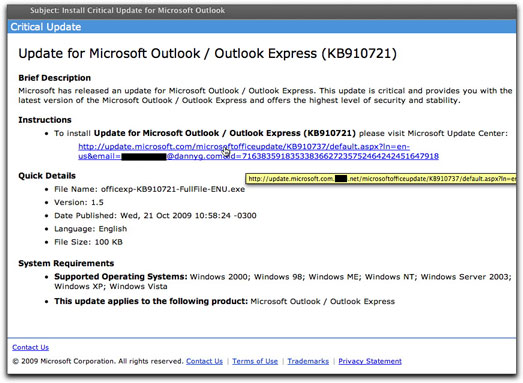
Another Round of Bogus MS Outlook UpdatesAn earlier campaign to infect Microsoft Outlook users (reported back in June of this year), must have been a success, because it's back. There are some subtle differences between the two email messages, one of which isn't so funny. Here's the new one:
Among the amusing differences is that, although the name of the malware delivery file mentioned in the message (officexp-KB910721-FullFile-ENU.exe) is the same, today's message shows that it is now the new and improved version 1.5 (instead of 1.4). Oh, goodie!
As before, the domain of the infection site was born yesterday, and the originator of the campaign hopes that recipients were also. At the destination page of the link, rather than using an automatic drive-by type of installation, the new web page encourages visitors to download and install the file. Better to get the victim involved, I suppose.
What troubled me even more about this particular effort is that the hidden link looks just like the visible one, with the exception of the additional malware delivery domain inserted after "microsoft.com". In other words. What you can't see in the image above (because it's cut off) is that the recipient's email address is submitted as part of the URL. All those attributes after the "?" symbol aren't needed to visit the malware page, but it could mean that the Bad Guy is capturing valid (and gullible) email addresses in the process. Valid email addresses are one currency of the underground spam economy. A click of that link could earn you a whole lot more spam and malware email messages, while Bad Guys trade and sell your address. Put that stuff into a balance sheet, and all you're left with is "net" liabilities.
Posted on October 21, 2009 at 09:38 AM