« A Mixed Message | Main | The Phisher Doth Protest Too Much »
| Home | The Book | Training | Events | Tools | Stats |
November 25, 2004
Phishing SpreeThe last few days have brought quite a few phishing messages my way. Looking back I see Well Fargo Bank, Suntrust, Western Mutual, eBay, and PayPal. They use a variety of URL cloaking techniques, but nothing new.
Since the Windows patch for one trick has been out for awhile, I thought the trick would go away. But it has shown up a few times recently. In unpatched Windows systems, the status bar view of the clickable link fails to show the full URL, only the bogus part that looks legitimate. In the message's source code view, you can spot these easily, like this one:
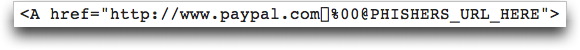
Those weird characters (following "paypal.com") fool unpatched Windows machines to hide themselves and everything after them. But when you click the link, the browser goes to the Bad Guy's Web site.
The other technique is more difficult to sniff out, because the click link goes to a real URL of a real Web site. Unfortunately, the Web site is usually a server that is set up insecurely (typically a small business, but sometimes even biggies) and has been cracked. The cracker has installed a special directory in which the phishing page and server processing code is located. The rest of the site works like normal, and the site's owner has no idea the hidden stuff is there, robbing unsuspecting visitor's of their identities. Over the years, I've alerted numerous site managers about the invasions and got them to remove the offending directory and change their passwords to keep intruders out.
Despite their frequently professional looks and seemingly earnest messages enticing recipients to give up information almost down to their shoe sizes, the source code of these messages contain lots of other clues that wouldn't fool any Spam Wars reader.
Posted on November 25, 2004 at 11:02 AM
