« Phony Invoice Malware Delivery | Main | Wire Transfer Malware Lure »
| Home | The Book | Training | Events | Tools | Stats |
November 09, 2011
Today at the Ol' Phishing Hole...Another day, another Bank of America phishing attempt. This one tries to work double-duty by phishing not only for your BofA login credentials, but also identity data for every credit card you own.
The email message is pretty standard phishing stuff (although the Subject: line and message body don't really connect):
From: Bank of America <support@bankofamerica.com>
Subject: Bank of America SurveyQJRPRKRVWE
As part of our security measures, we regularly screen activity in the system.
We recently contacted you after noticing an issue on your account.
We requested information from you for the following reason:
We have observed activity in this account that is unusual or potentially high risk.Please download the form attached to this email and open it in a web browser.
Once opened, you will be provided with steps to restore your account access.
We appreciate your understanding as we work to ensure account safety.Sincerely,
Bank of America Account Review Department[file: SurveyQJRPRKRVWE.html]
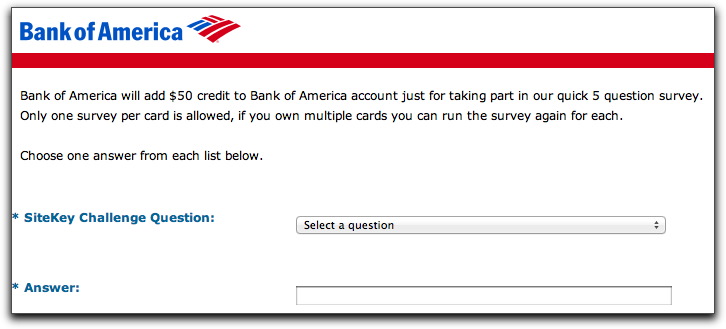
The file is, indeed, an HTML file, base64 encoded. That allowed me easy conversion offline to view the source code and see if it was safe to render in a browser (making sure it doesn't try to download any malware crap automatically). With the help of images downloaded directly from bankofamerica.com, the page starts out with the survey come-on:
Note that it encourages you to take the survey as many times as you have credit cards because supposedly you'll get fifty bucks in each card. Yeah, well....
The "survey" consists of six (not five) challenge question selections. I don't believe these questions/answers have anything to do with the phishing attempt.
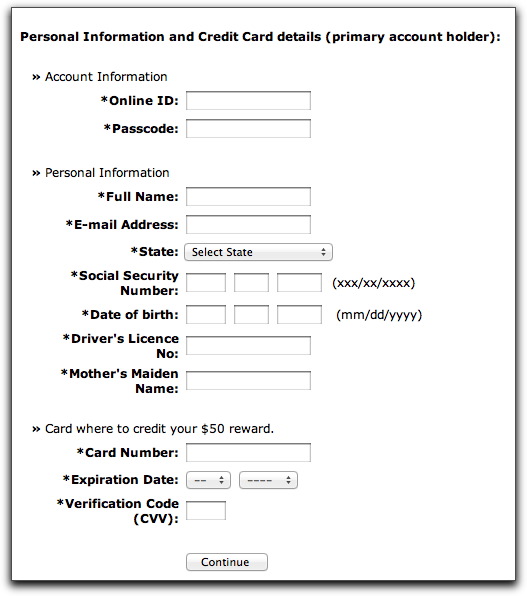
No, the real gold for this criminal comes in the latter portion of the page:
The most valuable info on the form are the BofA login credentials. With those two fields, the crook can clean you out. Credit card and other identity info are just sprinkles on the doughnut. If you were to fill out the forms (the HTML includes JavaScript that forces you to enter valid-looking info into the fields) and click the Continue button, the data goes to a PHP program running on a web server that has been hijacked from an established design firm in Russia.
And poof goes your bank account and identity.
Posted on November 09, 2011 at 10:39 AM