| Home | The Book | Training | Events | Tools | Stats |
February 21, 2006
Phisher Hopes You're OutragedI saw another installment of an old trick. An email message arrives acting as a receipt indicating that you have supposedly paid for something (usually an electronic gizmo) fairly expensive. In the past I've seen messages like this for $800 digital cameras and such. Today's message is for a $230 cell phone. The basic idea is to get the recipient so mad ("I DIDN'T BUY THAT THING!") that he or she immediately clicks on the link to get to the bottom of the snafu.
I've seen links in these messages lead to Web pages whose sole purpose is to install malware silently into the recipient's PC. The one I got today has a link to a phishing type of Web page with a form asking for everything but your shoe size.
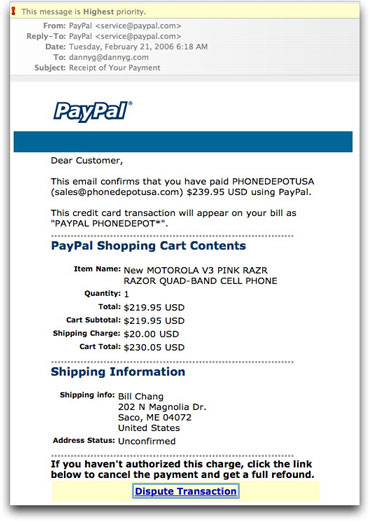
The email message is very convincing-looking:
There is one telltale sign that the message didn't source from PayPal in that it begins "Dear Customer." Real PayPal receipts address the customer by the full registered name. Of course even this information is fairly easily obtained from harvested email addresses that include your plain-language name along with address.
The only way you can tell that it is definitely bogus is by checking the email message's header (as I describe in Spam Wars). This message clearly did not begin its life at a PayPal email server. If there is any doubt at this point, however, a smart PayPal user would log into PayPal (not via any link in the message, but by either typing the full https:// address or using a previously saved bookmark to the real site) and check to see if PayPal showed any record of this transaction. You'd find that this transaction does not exist, and you are therefore not on the hook for $230.05.
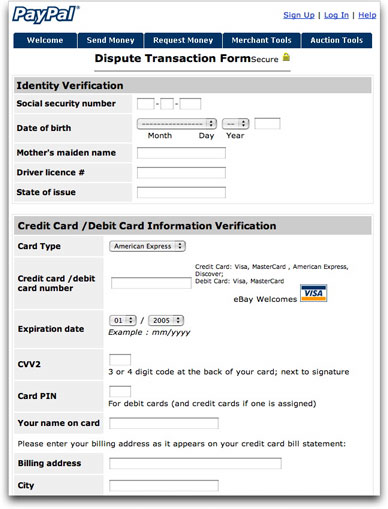
Failing good sense, a click of the "Dispute Transaction" link—a very hazardous thing to do in any case—leads to a Web page that also looks very convincing as a PayPal page:
There is enough personal information in this form for a chimp to impersonate you and give you a year or more of identity theft hell. The page also claims to be secure ("Lookie! We show a little padlock on the page!"), but the browser does not indicate a secure connection (and the URL is to a plain http protocol, not https one). The URL, by the way, is one of those numeric IP addresses. Like so many other phishing sites these days, the page was placed inside someone else's Web server. I guess you could call it a serverjacking.
Remember advice from the book: The more a message tries to provoke you to action (especially regarding financial stuff), the more likely it is a phony, even if, on the surface, it looks legit.
UPDATE: I just noticed that the arithmetic is incorrect in the "receipt." One should assume that by now, PayPal's computers know how to add. Phishers, on the other hand,....
Posted on February 21, 2006 at 09:24 AM