« Your Apple ID Has NOT Been Suspended | Main | Avoid Phony Dropbox File Sharing »
| Home | The Book | Training | Events | Tools | Stats |
November 18, 2015
How Bad Guys "Hack" NetworksEvery time I hear of a security breach at a personal, corporate, or government computer system, the first thing I want to know is how the crooks got into the system. Sadly, this information is usually missing from published reports. But based on the amount of unsolicited email like the one discussed below that keeps flooding the Internet, I maintain that most so-called break-ins are actually caused by individuals who essentially admit the crooks into the computers. For a variety of reasons, email recipients click on unknown links and attachments that install entryways into the computer. The crooks then have free reign of not only the private information on that particular computer (or, in some cases, mobile device), but also access to networks to which the PC connects. Even if the thieving piece of software gets installed while the user is running from a public network at home, the software can simply wait for the PC to be connected to an employer's network, where the real valuable stuff can be.
So, how does a recipient get tricked into installing this kind of badware?
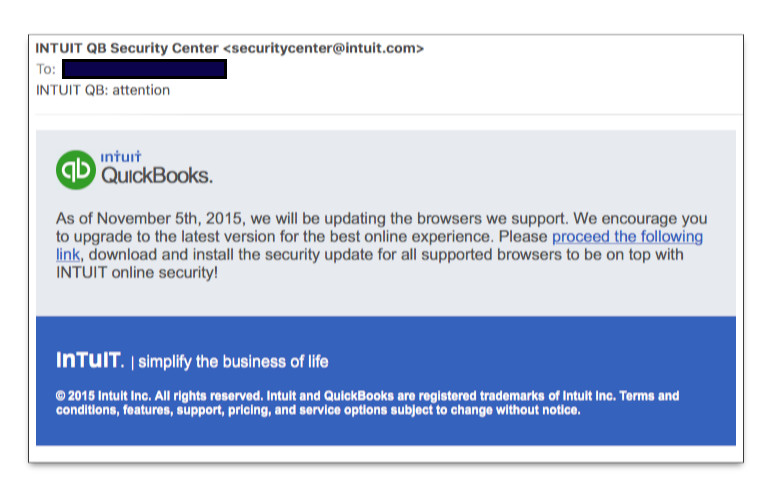
Here's an example that arrived today, claiming to be from Intuit's QuickBooks Security Center:
Admittedly a couple grammar errors mar the message (e.g., "proceed the following link", rather than "proceed to the following link"), but at first blush, the whole production looks pretty darned official. Plus, we poor computer users are so overwhelmed by a constant barrage of software updates, that we scarcely (at our peril) question requests to update this or that. Once the update starts, we also don't question the request for a system password because that's what official system updates often require. Unfortunately, the bogus request simply captures the password for later intrusions into the system—like handing a set of your house keys to a stranger walking down the street.
Clicking on email or web page links offers the feeling of doing something. At your desk at work, clicking looks like you're getting something done, letting you put on a good show that you're earning your wage. The problem is—as has been demonstrated time and time again through the history of this blog— a simple click can begin a cascade of problems that can cost literally millions to clean up (ask Sony).
And yet, with only a thimbleful of paranoia and perspicacity, any non-technical user can prevent a Bad Guy from getting into the system.
The paranoia entails suspecting every link that comes in an unexpected email message, regardless of how dire the message may sound (e.g., you're about to lose your account access).
The perspicacity entails rolling the mouse pointer atop a link (or, on a touchscreen device, pressing and holding on the link) to reveal the URL of the link's destination. In the case of the Intuit message, the link leads to (portions removed for your safety):
http://style[removed].com/system/logs/update/doc.php?r=download&id=INTUIT-Browser-up1247.zip
The domain of this link belongs to a Turkish medical products company. The site has been hijacked (most likely via the methods described earlier in this post) and now hosts malicious software disguised as an Intuit update—kind of The Circle of Death. The point is, the domain of the URL revealed by the rollover has nothing to do with Intuit or QuickBooks. That should ring all kinds of alarm bells.
If I had my way, I'd also want to teach the emailing world how to interpret email header gobbledygook. The first lesson is to know that lots of a header can be forged, especially the part that indicates the From: field, which can say anything without scrutiny and with impunity.
Buried within this particular message's header is the fact that the message originated from a DSL pool connection in Germany—a highly unlikely way for Intuit to send out a genuine security message. I'd wager that the message came from a German home computer that had previously been compromised through the same kind of malware trying to work its way onto the message recipient's computer. A Bad Guy had taken over that machine to send out the messages with the link to the hijacked Turkish web site. The German computer owner is none-the-wiser because today's PCs and broadband connections are fast enough to not get bogged down by becoming bots for evil doers.
Still, the weakest link in the entire chain between Bad Guy and compromised business computing networks is the typical PC user who falls for tricks like the one shown above. Security technologies have limits, which means that we cannot rely on them to perform 100% of the job of keeping our PCs criminal-free. Resisting the urge to click on an unknown link or attachment seems to be an enormous challenge. It's counterintuitive to think of not doing something as being the most valuable thing you can do.
Posted on November 18, 2015 at 12:48 PM