| Home | The Book | Training | Events | Tools | Stats |
May 28, 2019
We Need You. Let Us Ravage Your NetworkMost online crooks are not picky about what company they want to infest with malware. The key is to trick some poor soul at the company to double-click the attached file to get the malware installed on anybody's PC at the company with an internet connection.
Once the malware is installed, some crooks sell access to that malware to other crooks who then root around the personal computer on which the malware is installed and to whatever local area network the PC might be connected. Because the malware easily snarfs up the PC user's username and password for email or other services, it is then a walk in the cyberpark to find other services running on the network. Sometimes it's product development details, sometimes it's bank account access, and sometimes it's payroll activity or emails (remember Hillary?). Or, depending on the crook, they might encrypt the entire network storage system, holding the data hostage until your company pays ransom.
So, once the crook's email message gets past whatever filtering might be on the email server, how does a crook get past the first line of defense: the hapless employee who wants the company to succeed? Simply make up a story that lets the employee think he or she will be a hero by responding to a new customer hungry for the company's products or services.
[By the way, the "hapless employee" is just as likely to be a top executive as a low-level worker. In fact, the Chief Whatever may believe that he or she is smarter than the average drone, and wants to be just as big a hero. Know-it-alls are the first to be compromised.]
That's the idea behind the following malware delivery email message. The Subject: line reads:
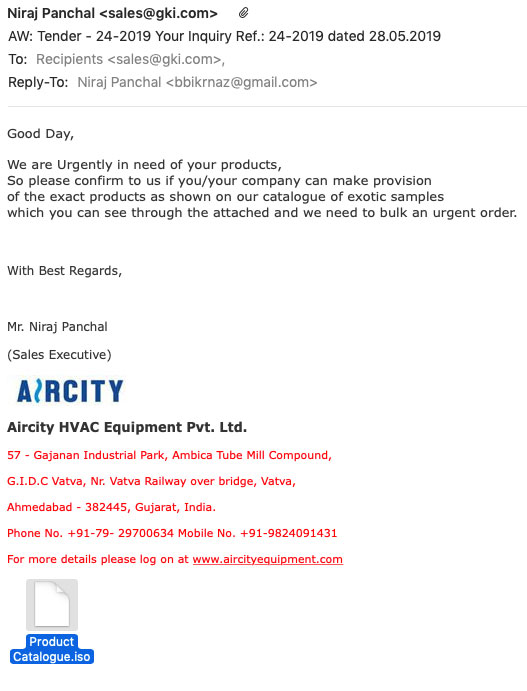
AW: Tender - 24-2019 Your Inquiry Ref.: 24-2019 dated 28.05.2019
This was a little unfortunate for the crook because the "AW" in the front is German for "RE", for a typical email message reply. He's trying to make it look as though the recipient has already had some communication with the guy, and everything is safe.
Here's the entire message:
The body is a decent example of a slightly distorted English message one might expect from a correspondent in India. And then there's the official-looking logo art and full identification block with physical address, phone numbers, and web site of a real company by that name. Unlike some crook invasions, it doesn't appear as though the actual Indian company's web site has been hacked because no nefarious links to the web site are embedded in this message. Instead, the bad stuff is all in the attachment.
The attachment is a file with an .iso extension. This type of file is an image of a mountable Windows disk volume. I have no idea what's on that volume, but double-clicking the file and allowing it to mount would be as dangerous as plugging in an unknown thumb drive into your PC. There is likely self-executing code that installs all the necessary loaders to let others clog up the works and start grabbing data.
Unfortunately, as I write this, VirusTotal shows detection of this file as malware in only five antivirus programs. My guess is that this file has been slightly modified from a tried-and-true piece of malware, but just enough to avoid signature detection by antivirus programs (called a zero-day attack).That's how an email message like this could get past malware filters on email servers and antivirus programs on PCs whose user double-clicks on it.
There is nothing new here, but it's important to keep this type of activity fresh in your mind to be highly suspicious of any email message containing an attachment you weren't expecting. In this case, you wouldn't be the hero saving your firm, but rather the goat that lost the company valuable private data and perhaps payroll for the next pay period. Your colleagues won't be too happy about that.
Posted on May 28, 2019 at 04:22 PM